
Inadequate authorization checks gaps/weaknesses that allow unauthorized users to view, modify, or delete sensitive infor...
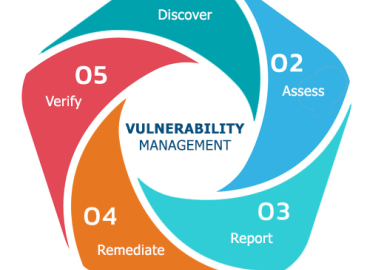
Web sites use open source tools to help manage and edit web files. Since the code is open source, security vulnerabiliti...
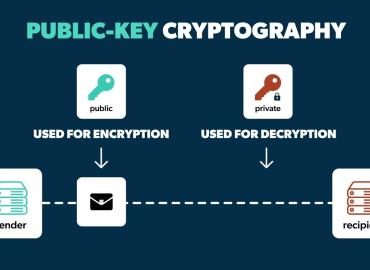
Occasionally, when diagnosing mock hacking on a mobile app or website, there are cases in which the data is encrypted wi...

Many IoT devices such as dual-mode routers, IP cameras, and door locks provide their management services, such as provid...

SQL injection is an attack technique in which an attacker exploits security vulnerabilities to inject and execute arbit...

Cross-site scripting (XSS) is an attack method that contains malicious scripts on a web page and is placed on the user's...

Command Injection is a vulnerability in which unintentional system commands are executed by user input values that have ...

An overflow vulnerability occurs when a program that uses contiguous memory space tries to read or write data to a loca...

File download and execution vulnerabilities refer to weaknesses that arise from the capability of ActiveX to download e...