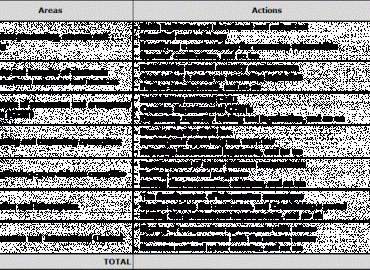
Tax Administration of Kosovo (TAK), as Enforcement Agency with full Autonomy, is responsible to administer the implement...
CLIENT A company (oil refinery) BACKGROUND AND TOPIC - As a global company, it operates a large number of informa...
There was a consulting request from the client company for the AD security policy. AD security policy can be seen fro...
CLIENT The Ministry of Information and Communication of Moldova NATIONAL ICT STATUS The Republic of Moldova, which...

CLIENT A refinery (refinery) PROJCET BACKGROUND AND TOPIC As a representative company in the petroleum industry, th...

Most of the application source vulnerability diagnoses will receive a large number of source files and perform vulnerabi...

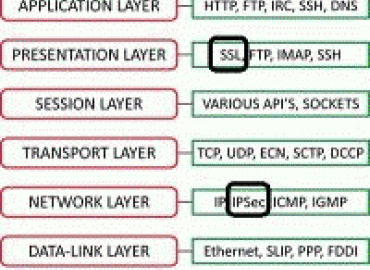
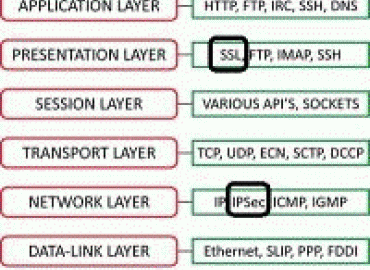
VPN has various methods such as remote access from site-to-site. However, from the viewpoint of an attacker, it is an a...

* There are many purposes to hide your IP. - When Google pulled out of China, there were a lot of Chinese who used publ...
