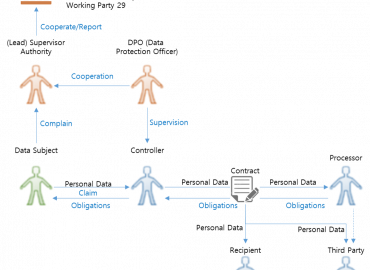
In the digital age, data protection has become a paramount concern for both businesses and individuals. Rwanda, cognizan...
The CyberTech Africa Conference is an important cybersecurity and information technology event held annually in Africa. ...

The 2022 / Tanzania ICT Commission recognize the importance of cybersecurity at the national level, and as part of this,...

"The 2018 Kosovo/TAK's Adaptive Security System Development Pilot Project" which carried out for seven months through Ma...

In order to share our experiences and know-how of Cyber Security in Korea with peoples in the blind spot of information ...

WiKi Security Corporation, which participated in TAS(Transform Africa Summit) 2018, the largest ICT event in Africa, as ...

The Ministry of Information Technology and Communication (MITC) is a central specialized public administration body whic...

Philippines NTC is an attached agency of the Department of Information and Communication Technology, responsible for th...

Rwanda's Telecom, KT Rwanda Networks Ltd, is a communications company with Rwanda's only LTE communications infrastructu...