OVERVIEW
Roles of Vendor and User in S/W Supply Chain Security.
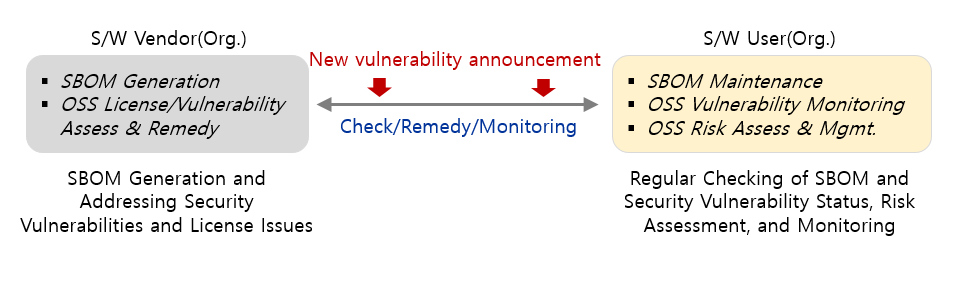
In the S/W Supply Chain, a management system that divides the roles of S/W Vendors and Users is essential for managing the security and compliance of open source software. The S/W Vendor is responsible for generating the SBOM (Software Billof Materials) for the open source components used in thedeveloped software, addressing license issues and eliminatingsecurity vulnerabilities before distribution. The S/W User, on the other hand, is responsible for regularly checking the SBOM received from the Vendor for newly disclosed security vulnerabilities and license issues to ensure compliance.
From the S/W User’s perspective, it is inevitable that new security vulnerabilities will be discovered during the receipt or use of the software, even with the SBOM and security vulnerability elimination results provided by the Vendor. This is because the SBOM generation cycle of the S/W Vendor and the disclosure cycle of security vulnerabilities are different. Therefore, it is wise for the S/W User to regularly check and assess the security vulnerabilities of the open source components registered in the SBOM provided by the Vendor and respond to compliance and threats accordingly.
Strategy for S/W User
Cost-effective Strategy for S/W User.
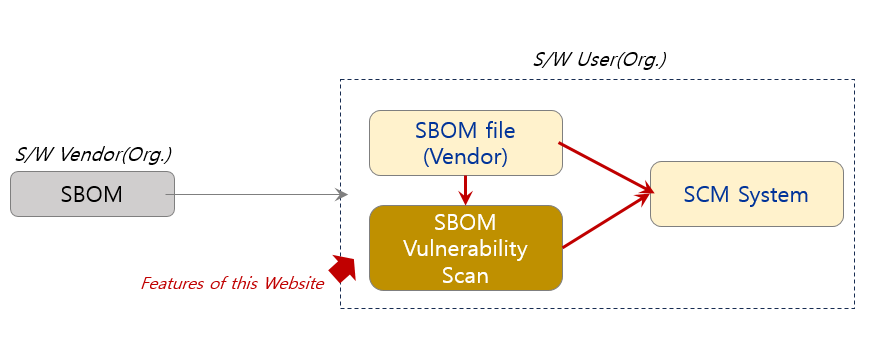
One of the cost-effective strategies for S/W Users in securing the S/W Supply Chain is integrating the SBOM Vulnerability Scanner with the organization’s SCM (Software Configuration Management) system to address S/W Supply Chain security compliance and threats. In other words, by regularly scanning the SBOM received from the S/W Vendor for security vulnerabilities, monitoring, and requesting the removal of vulnerabilities, the SBOM Vulnerability Scan engine is utilized. The organization uses its SCM system to maintain and manage the configuration of the SBOM files and vulnerability scan result files provided by the vendor.
This website offers an SBOM Vulnerability Scan engine that anyone can use. It allows users to upload the SBOM provided by the manufacturer to scan for known security vulnerabilities in the open source components listed in the SBOM and generate the results in CSV (or JSON) format for integration with the organization’s SCM system.
HOW TO USE
Step 1. Click the textbox to open a Windows Explorer window and select the SBOM file in JSON format.
Step 2. Click the ‘SUBMIT’ button to submit the selected SBOM file.
Step 3. View the security vulnerability scan results for the open-source packages in the submitted SBOM file.
* The database used to scan for security vulnerabilities in open source packages is updated daily to maintain up-to-dateness.
* The screen below shows the security vulnerability scan results for a sample SBOM file.
