OVERVIEW
WiKi-MONSTER is developed for centralizing, analyzing and intrusion monitoring based on logs and network packets information from network devices, servers, IDS/IPSs, and firewalls with client-server architecture(sensor and server).
CORE FEATURES
Centralized log management and analysis
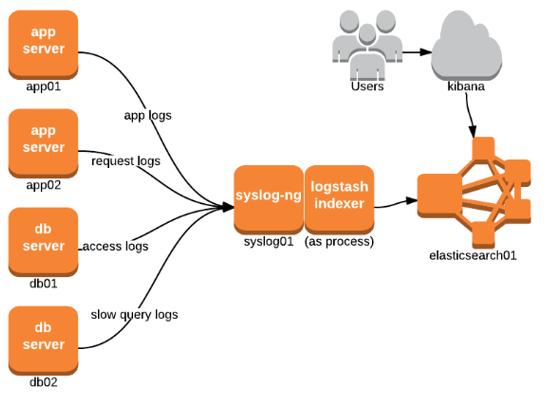
The WiKi-Monster uses syslog-ng as its primary syslog collector and to send logs to Logstash where they are parsed and augmented before being written to Elasticsearch.
Full packet capture and store (forensic features)
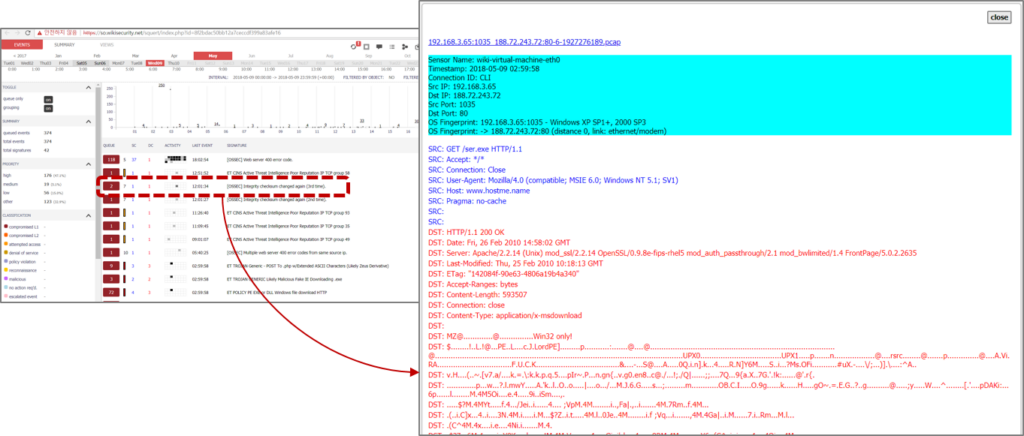
Full packet capture is like a video camera for your network, but better because not only can it tell us who came and went, but also exactly where they went and what they brought or took with them (exploit payloads, phishing emails, file exfiltration). Our WiKi-Monster collects and stores all the packet data collected by the sensor, so you can check the event by inquiring the specific packet of the specified date.
Network-based and host-based intrusion detection systems (NIDS and HIDS)
Network-based and host-based intrusion detection systems (IDS) analyze network traffic or host systems, respectively, and provide log and alert data for detected events and activities.
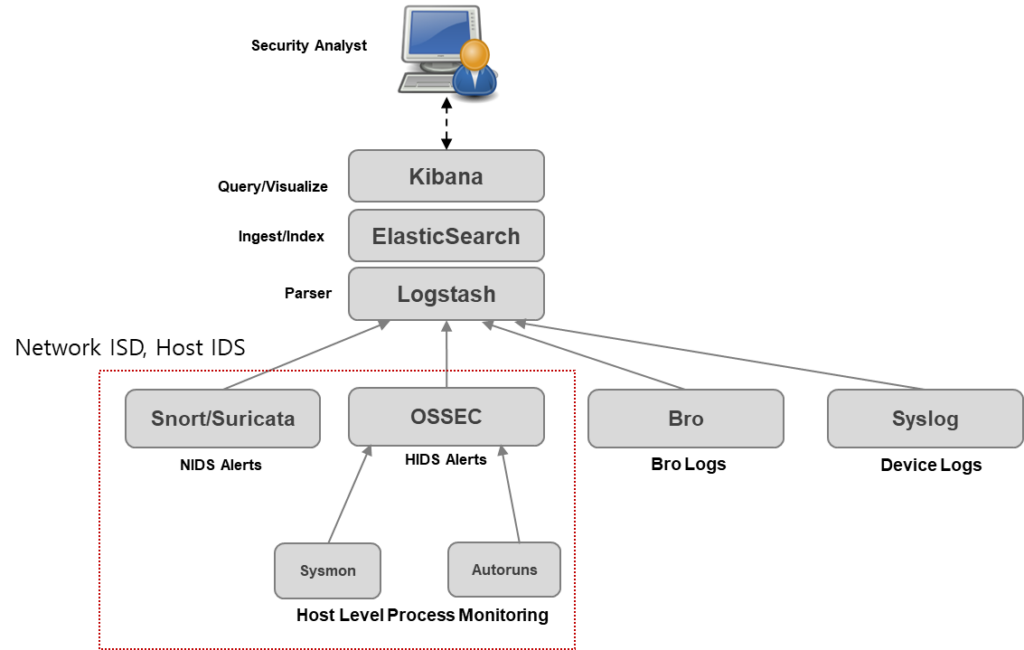
Powerful analysis tools
With full packet capture, IDS logs and Bro data, WiKi-Monster is provide various analysis features to analyst such as security engineer, security monitoring engineer, and security manager
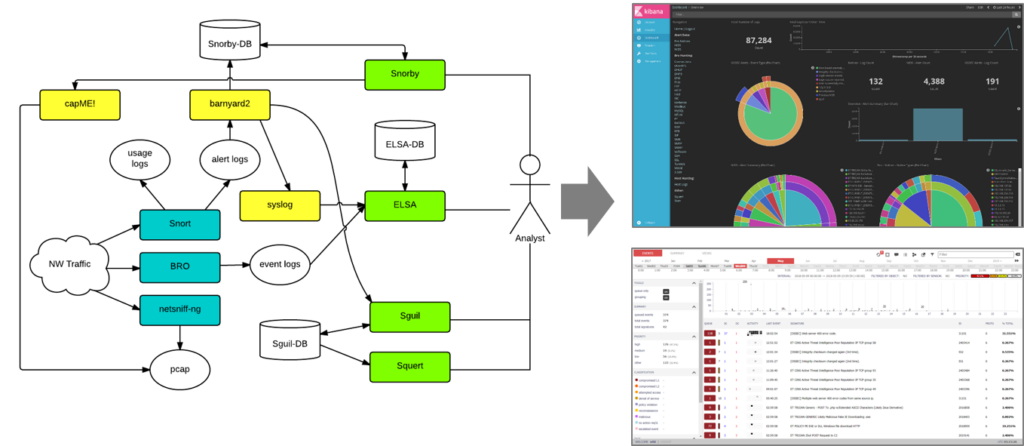
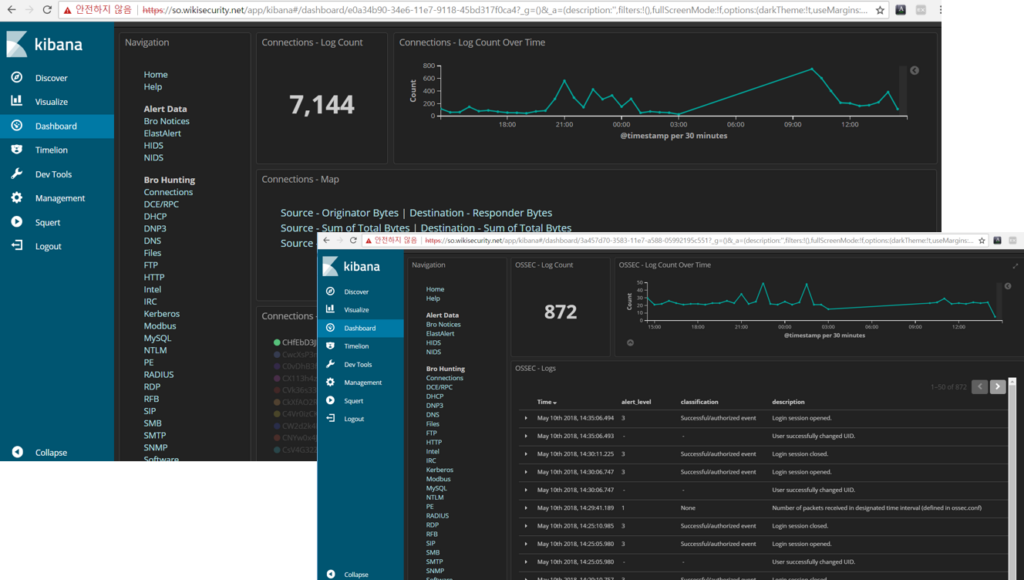
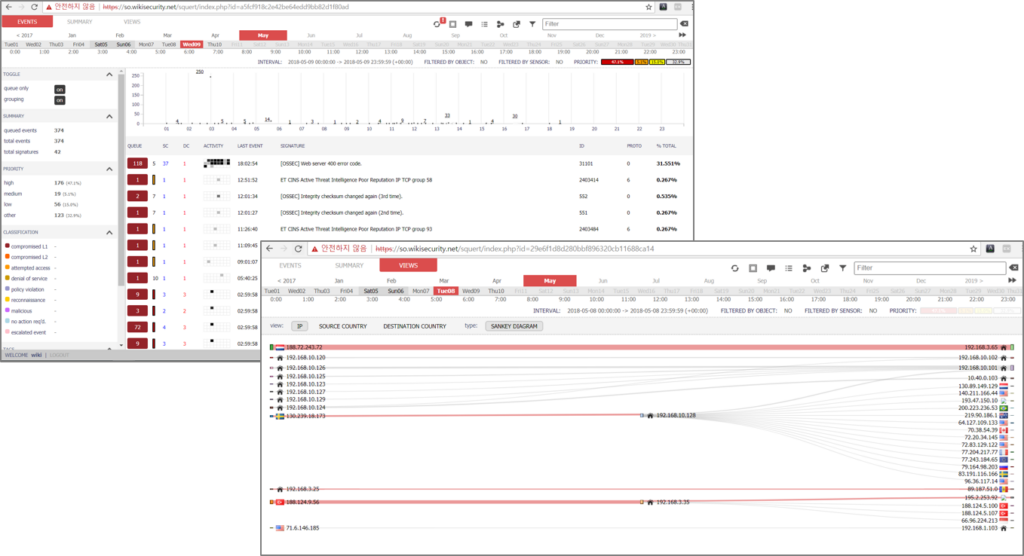
SCREEN SHOTS