
Inadequate authorization checks gaps/weaknesses that allow unauthorized users to view, modify, or delete sensitive information without going through a valid authentication process when submitting a request to a website. For example, when you edit an article on an ad, the following HTTP request is sent.
read more
Web sites use open source tools to help manage and edit web files. Since the code is open source, security vulnerabilities can also be easily discovered, Therefore, developers/individuals need to be careful when using open source because security is open to all.
read more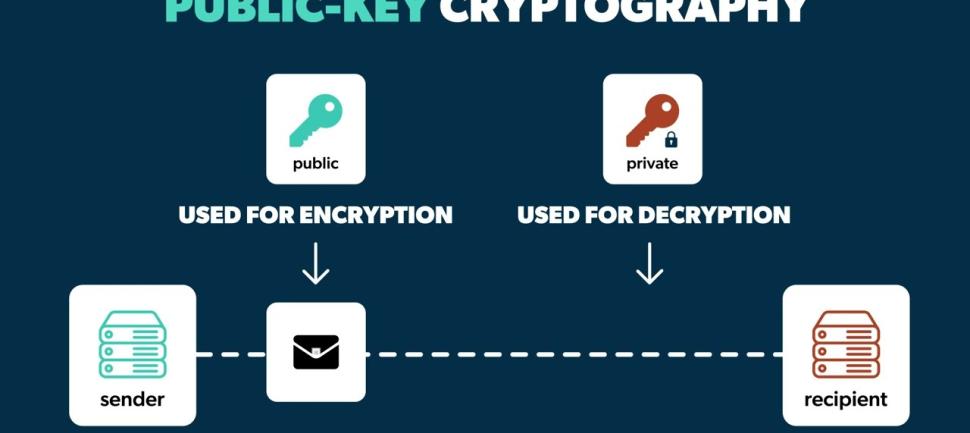
Occasionally, when diagnosing mock hacking on a mobile app or website, there are cases in which the data is encrypted with a random symmetric key method and transmitted to the server without encrypting the data using the public key of the server.
read more
Many IoT devices such as dual-mode routers, IP cameras, and door locks provide their management services, such as providing information or changing settings, through web pages using HTTP. These management pages come from CGI files that are already compiled into the firmware
read more
SQL injection is an attack technique in which an attacker exploits security vulnerabilities to inject and execute arbitrary SQL statements, thereby manipulating the database to perform abnormal operations.
read more
Cross-site scripting (XSS) is an attack method that contains malicious scripts on a web page and is placed on the user's side. For example, if an unverified external input value is used to create a dynamic web page, visitors to that web page will immediately see the attacker's identity and information about the target web page.
read more
Command Injection is a vulnerability in which unintentional system commands are executed by user input values that have not undergone proper verification procedures, which can inappropriately change user privileges or adversely affect system operation and operation.
read more
An overflow vulnerability occurs when a program that uses contiguous memory space tries to read or write data to a location beyond the allocated memory range. By causing program malfunction or executing malicious code, an attacker gains the authority to control the program.
read more
File download and execution vulnerabilities refer to weaknesses that arise from the capability of ActiveX to download external files. These methods are typically employed to execute functions within ActiveX or to substitute a specific module.
read more