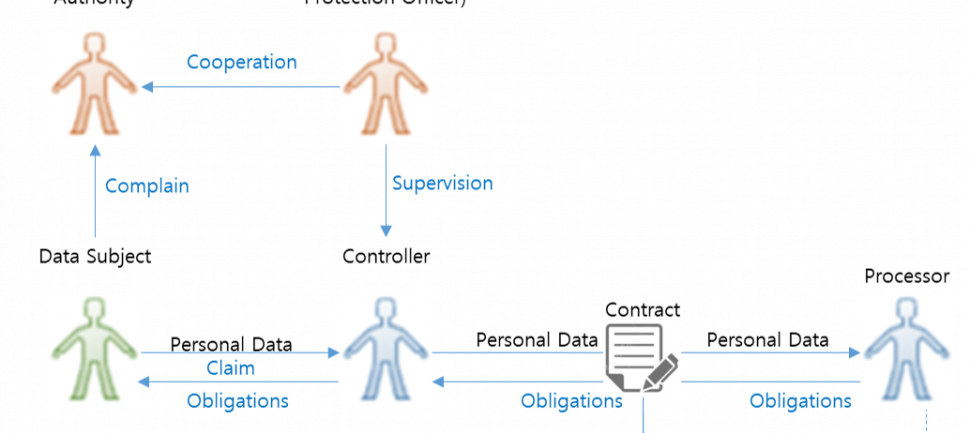
In the digital age, data protection has become a paramount concern for both businesses and individuals. Rwanda, cognizant of these shifting paradigms, introduced the Data Protection and Privacy (DPP) Law, setting standards and guidelines for businesses operating within its jurisdiction.
read more