There was a consulting request from the client company for the AD security policy.
AD security policy can be seen from various points of view from design of AD to account management, but since the total number of accounts is over 100,000, this consulting focused on identifying the latest issue, abnormal account, and suggesting improvement plan.
For example,
- a bad pwd count attribute value is significantly higher
- Accounts with significantly older last logoff attribute values
- An account with no password required
- An account with password never required
Is an attack target account, or an account that is exposed to dormant accounts or potential risks, so it is an account that needs to check deeper account issuance and settings.
In order to retrieve a large number of account attribute values, we used Powershell Script to save them as Excel and analyze them from various perspectives. In this section, we focused on matters that should be taken into account when checking UAC (User Account Control).
Typical attributes of UAC are as follows.
- Enable / Disable User and Computer Accounts
- Account Lockout
- User Can not Change Password
- Computer Account Types
- Password Expiration
- Smart card required for logon
In addition to the above properties, there are a number of things, and these values are set to integer values, so if you want to query Powershell script, you should write script based on the flag table as below.
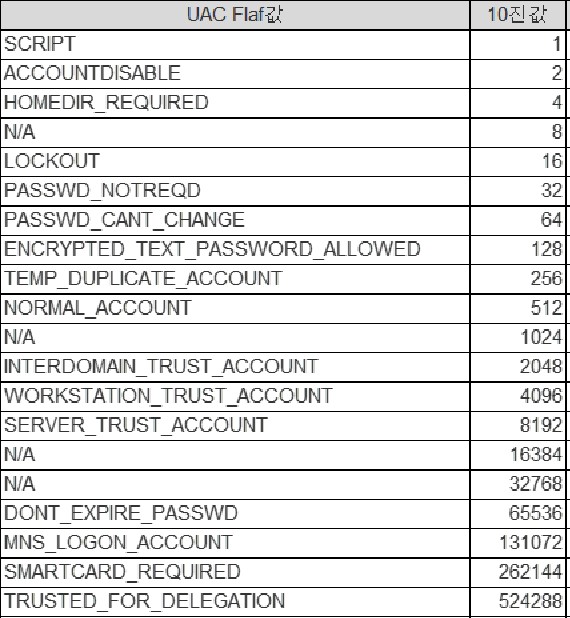
If you are logged in to the AD Domain controller, the script will be simpler by importing the AD module. However, since the vulnerability diagnostic environment does not cooperate so well, the script created without the AD module has only one AD Domain User account. It gets longer.
As shown in the figure above, the UAC flag value is actually stored as a decimal number, which is the same as the square value of 2. Therefore, Powershell Script that branches according to UAC flag value of account can be written as below. Queries for all accounts can be searched using the for each function and counted together to derive lists and sums of abnormal accounts.
$Power = 26
Do
{
$Test = [Math]::Pow(2,$Power)
If (($Num - $Test) -ge 0)
{
Switch ($Power)
{
26 {Write-Host "ADS_UF_PARTIAL_SECRETS_ACCOUNT"}
24 {Write-Host "ADS_UF_TRUSTED_TO_AUTHENTICATE_FOR_DELEGATION"}
23 {Write-Host "ADS_UF_PASSWORD_EXPIRED"}
22 {Write-Host "ADS_UF_DONT_REQUIRE_PREAUTH"}
21 {Write-Host "ADS_UF_USE_DES_KEY_ONLY "}
20 {Write-Host "ADS_UF_NOT_DELEGATED"}
19 {Write-Host "ADS_UF_TRUSTED_FOR_DELEGATION"}
18 {Write-Host "ADS_UF_SMARTCARD_REQUIRED"}
17 {Write-Host "ADS_UF_MNS_LOGON_ACCOUNT"}
16 {Write-Host "ADS_UF_DONT_EXPIRE_PASSWD"}
13 {Write-Host "ADS_UF_SERVER_TRUST_ACCOUNT"}
12 {Write-Host "ADS_UF_WORKSTATION_TRUST_ACCOUNT"}
11 {Write-Host "ADS_UF_INTERDOMAIN_ TRUST_ACCOUNT"}
9 {Write-Host "ADS_UF_NORMAL_ACCOUNT"}
8 {Write-Host "ADS_UF_TEMP_DUPLICATE_ACCOUNT"}
7 {Write-Host "ADS_UF_ENCRYPTED_TEXT_PASSWORD_ALLOWED"}
6 {Write-Host "ADS_UF_PASSWD_CANT_CHANGE"}
5 {Write-Host "ADS_UF_PASSWD_NOTREQD"}
3 {Write-Host "ADS_UF_LOCKOUT"}
2 {Write-Host "ADS_UF_HOMEDIR_REQUIRED"}
1 {Write-Host "ADS_UF_ACCOUNTDISABLE"}
0 {Write-Host "ADS_UF_SCRIPT"}
}
$Num = $Num - $Test
}
$Power--
} While ($Power -ge 0)
|