Vulnerability example
Web sites use open source tools to help manage and edit web files. Since the code is open source, security vulnerabilities can also be easily discovered, Therefore, developers/individuals need to be careful when using open source because security is open to all.
Once an attacker has confirmed that an open source library has been installed on a particular site, the attackers often exploit the security of the known site. For example, as shown below, an attacker checks that an open source library for a file management program is used in a video downloaded from a certain technology website, or uses it to attack a known location. After that, in the open source code, there are many problems. where security updates are not done, there are vulnerabilities that may be in files, codes, etc. and are used by other developers.
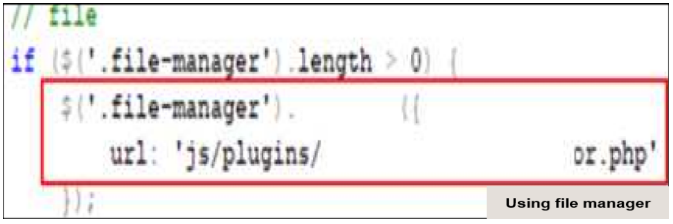
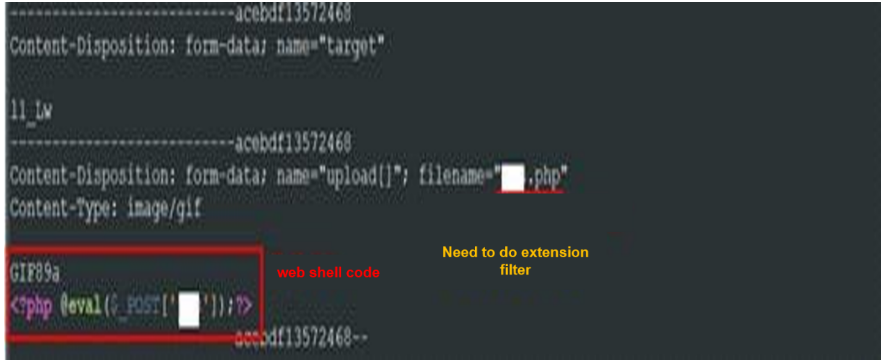
The attack finds a vulnerability in open-source software that does not check the file extension when sending a file. Using this,
you can change some of the required http request values requested from the server when you upload the file like this, upload the web shell .php file, and run the web shell to check the server.
How to Fix this Problem
In-house code security is required if there are no third parties to provide support (technical support companies or open source community participants).
Continue to request security information by monitoring KrCert, NVD (US Vulnerability DB), OSS community and etc.
It is recommended to change only the allowed extensions that are sent so that the controlled extensions can be changed.
The search path (../, ..\, \.., ./, .\, etc.) should be filtered to prevent the current file permission from being changed to a file used by the attacker.
Be careful as file transfer attacks can be overridden by unknown methods if the control part is done as shown below:
V3 = this // path
while (check(“\\..\\”, &a);
...
while (check(“\\.\\”, &a);
while (check(“\\\\”, &a);
// In this case, it is possible to bypass the path detection
Attackers, except asp, cgi, php, js pextensions, uknown.cer, use extensions like .asa, cdx, hta, phar, and aspx.
In addition, it is possible to attack using the process extension case replace (.Jsp ), Null Byte ( .jsp%00.jpg ) and double extensions, it is recommended to check everything and cover every vulnerability. In the case of open source, a patch is not required that can block all vulnerabilities.
If the attacker can change the functionality of the function to enable bypass, the attack can be caused by exploiting the same vulnerability as before.