
Cross-site scripting (XSS) is an attack method that contains malicious scripts on a web page and is placed on the user's side. For example, if an unverified external input value is used to create a dynamic web page, visitors to that web page will immediately see the attacker's identity and information about the target web page.
There are different types of cross-site scripting attacks, such as Reflected XSS, Stored XSS, and DOM xSS.
As an example of this type of XSS vulnerability, after placing the image on the bulletin board as shown in the image below, enter the script syntax in debug mode and send it.
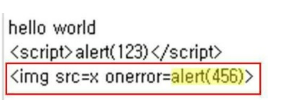
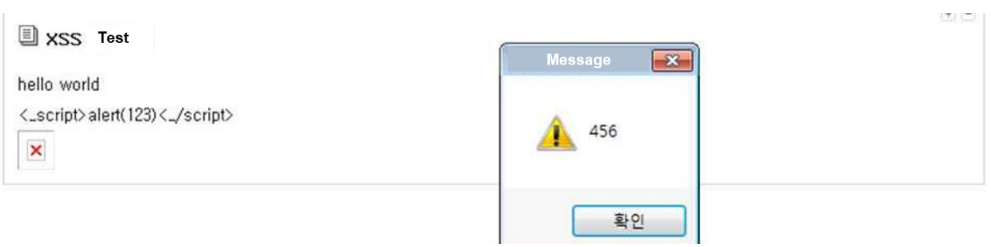
When you go back and check the post again, this <script> tag is shown in the image below.
Although it looks like a <_script> variable, it is sent in script syntax and inserted into the image where the <IMG> tag is executed on the client's computer.
These attackers modify the code and syntax in the following way and attack the <script> tag filter which is executed using the following functions String.fromCharcode() function in the syntax errors.
with(top.documnet)body.appendChild(createElement(‘script’)).src=‘Malicious Behavior Page’;
How to fix these errors
Variables need to be declared and initialized to prevent exploitation in XSS script syntax JSTL or well-known anti-cross-site script libraries.
In the mode that accepts HTML tags, these are the only tags used after creating a whitelist of valid HTML tags.
if($wr_a)
$sql_a= “ and wr_a=’$wr_a’ “;
$re_text = <span style=’font-weight ...
else {
$sql_a = “ and wr_a=’0’ ”;
$re_text=“”; // If the variable is not declared, the attack succeeds if the filtering section is bypassed when entering the XSS syntax
In addition to the commonly known parts such as special characters, HTML tags, attributes, and CSS, filtering includes parts that can be bypassed to prevent scripts from being inserted into external input or output values.
What we can add to the generalization of non-standard characters, HTML tags, attributes, and CSS, there are filter elements to prevent/stop scripts from entering from outside or inside the code.
private String cleanXSS(String value) {
value = value.replaceAll("<", "<").replaceAll(">", ">");
value = value.replaceAll("\\(", "(").replaceAll("\\)", ")"); value = value.replaceAll("'", "'");
value = value.replaceAll("eval\\((.*)\\)", "");
value = value.replaceAll("[\\\"\\\'][\\s]*javascript:(.*)[\\\"\\\']", "\"\""); value = value.replaceAll("script", "");
return value;
- When you include html tags, INPUT, IMG, svg, and IFRAME filtering becomes necessary.
- In addition to commonly known keywords such as onerror, onload, and onclick, action keywords that can cause XSS attacks, such as onfocus and autofocus, should be carefully considered and avoided in order to prevent them from being used in attacks.
- When parsing a specific extension, it is important to check if XSS logic is included.
- It is important to protect the code execution by converting it to hexadecimal code etc…
- They are difficult to control by yourself, using security libraries and classes for each development environment such as ASP.NET: MS Anti-XSS, MS AntiXSSEncoder, HTML Sanitizer library JAVA: Lucy-xss-servlet-filter, OWASP ESAPI library PHP: HTML Purifier library