
Vulnerability examples
Inadequate authorization checks gaps/weaknesses that allow unauthorized users to view, modify, or delete sensitive information without going through a valid authentication process when submitting a request to a website. For example, when you edit an article on an ad, the following HTTP request is sent. The website creates a unique profile for each document, and stores it in a database or a similar database. Then, when a change request is made to a position, the system compares the unique stored attributes with the value requested by the user before processing.
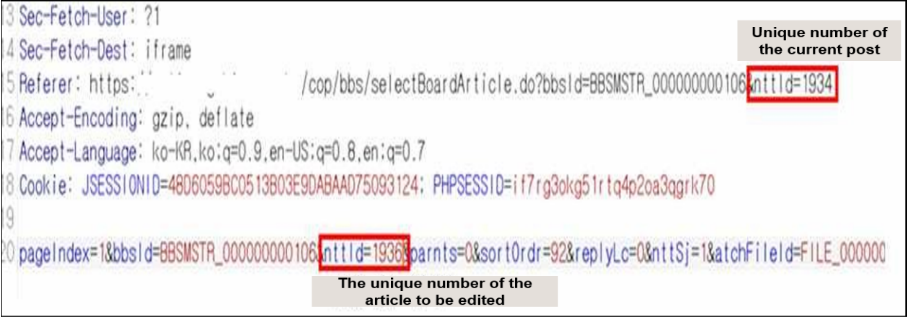
If the authentication system is only based on the unique ID of the document, an attacker can use a proxy tool to change the document number and modify the entries of other users.
How to Fix Weaknesses/gaps
Strengthen user control on the page that controls important information (personal information about the page, sending private messages, etc.) Check if the login ID on the page matches the login ID.
and confirm.
String userId = (String) session.getAttribute(“userId”);
String passwd = request.getParameter(“oldUserPw”);// Security code to check whether the actual requesting user matches the logged-in user
String requestUser = memberMode.getUserId();
if(usrId != null && requestUser != null && !userId.equals(requestUser)){
...
Implement secure per-user session authentication. Provide a one-time session ID with the appropriate length (one-time session ID) and complexity for each user, and verify that the session ID matches the request the user made.
There is a way to check if the value of the data from the client is associated reliably on the server side, not on the client side.
