
Vulnerability Examples:
Command Injection is a vulnerability in which unintentional system commands are executed by user input values that have not undergone proper verification procedures, which can inappropriately change user privileges or adversely affect system operation and operation.
For example, when the program is executed as shown in figure below, a specific string is transmitted through the custom protocol handler (wiki://). The string is a hexadecimal string encoding of the value encrypted by Blowfish.
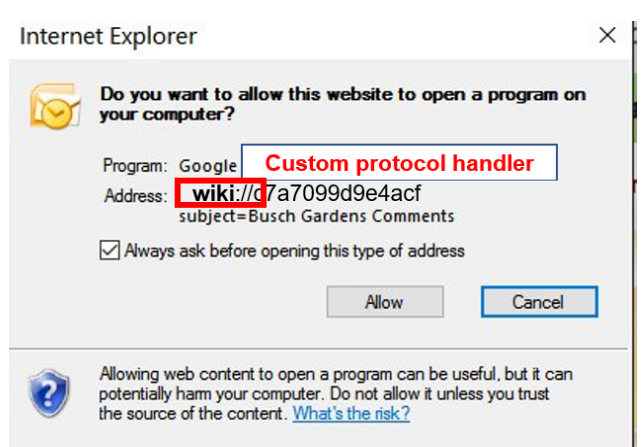
The decrypted string is separated by the strtok() function and stored in several variables, and the variable is finally used in the string passed to the ShellExecuteA() function and executed as an argument value, as shown in the figure below.
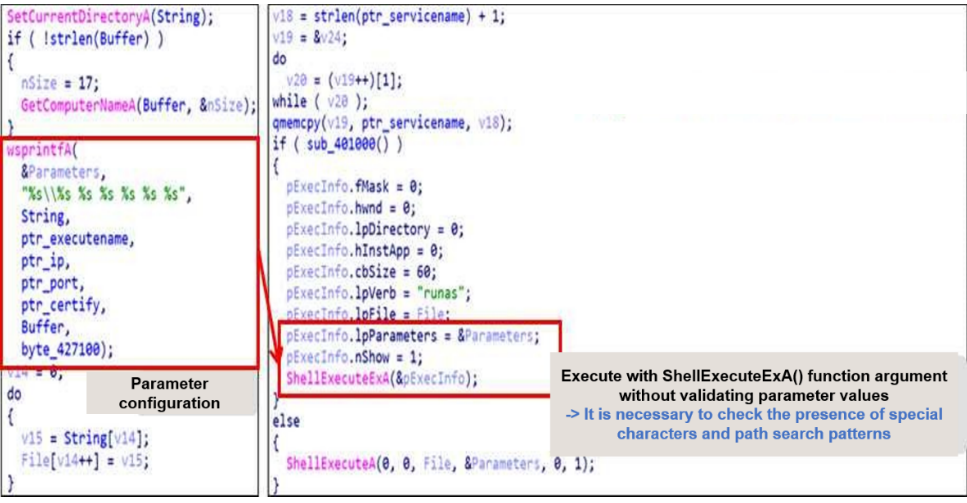
wiki:%00%00../../../../windows/system32/cmd“.exe
// Bypass verification by encrypting the same with a key hard-coded in the program afterwards.
If a user accesses a web page with a malicious command inserted in the custom protocol handler, it can be infected with malicious code, so it is necessary to verify the string before execution.
How to Fix Vulnerabilities
When identifying system resources (IP, PORT number, process, memory, file, etc.) using external input values, unauthorized resources must be prevented from being used.
- Define a list of resources to be used when designing functions, and select and use resources within the specified scope
- Management to minimize program modification when resource information is changed by defining it as a file or XML file
Creates a shell in the server program to prevent malicious commands from being executed by external input values when commands need to be executed
- Refrain from using shell execution functions (ShellExecuteW(), ShellExecuteExW(), ShellExecute(), etc.)
- Measures to ensure that external input values are not directly used as part of the command when a shell execution function is absolutely necessary
- List the values to be used as part of the command and take measures so that the command can be assembled and executed only with the values in the list
- If the listed values need to be changed in some cases, use a property file or XML file to create a white list so that the program is not modified.
Requires filtering of path search patterns (../, ..\, \.., ./, .\, etc.) for external input values
Be careful as it is possible to bypass and attack with an undetected pattern if only part of the verification is performed as shown below.
// Bypassable filtering example
V3 = this; //path
while (check(“\\..\\”, &a);
...
while (check(“\\.\\”, &a);
while (check(“\\\\”, &a);
// In this case, you can bypass the path detection pattern with \..\ or \../ to access the parent file.
Even if an input value (command in the handler) is encrypted with a hardcoded key in the program, if a third party (attacker) encrypts the malicious command with the same hardcoded key found through reverse analysis of the program, it can be bypassed and executed.
- Do not use a constant (hard-coded) encryption key inside the source code)