Vulnerability Examples:
An overflow vulnerability occurs when a program that uses contiguous memory space tries
to read or write data to a location beyond the allocated memory range. By causing program
malfunction or executing malicious code, an attacker gains the authority to control the
program.
Most of the vulnerabilities are caused by copying into memory without verifying the size
value and actual data size of a specific field in the file name or file format.
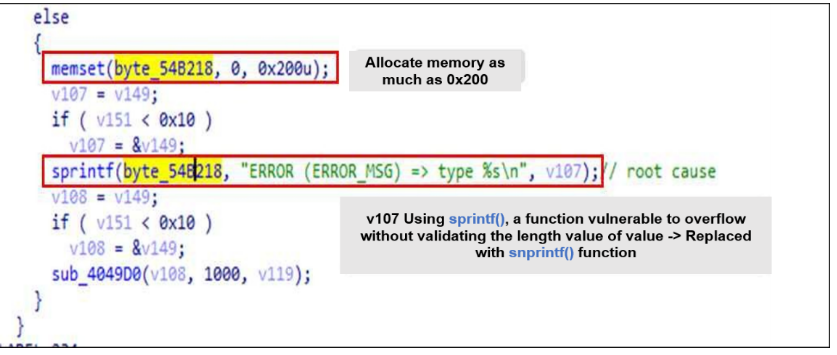
As a representative example, below is a code that records logs when the type value in the
json data is incorrect while the application program receives json data through the HTTP
handler. At this time, the buffer (byte_54B218) that stores the error message is set to 0x200
(512 bytes), and the type value (v107) is being copied to the buffer through sprintf(), a
function vulnerable to overflow, without length verification.
The heap spray technique is a method of delivering a payload. It allocates a large amount of
memory in the heap memory area and inserts code as if it were sprayed. Therefore, it is possible to
insert shellcode into a predictable memory area for heap memory. This is an attack technique officially
introduced in 2001 due to the vulnerability of MS01-033, and although it is an old technique, it is still
widely used today. When inserting data, a commonly used method is to use a combination of a large
number of NOP codes and shell codes that perform targeted attacks.
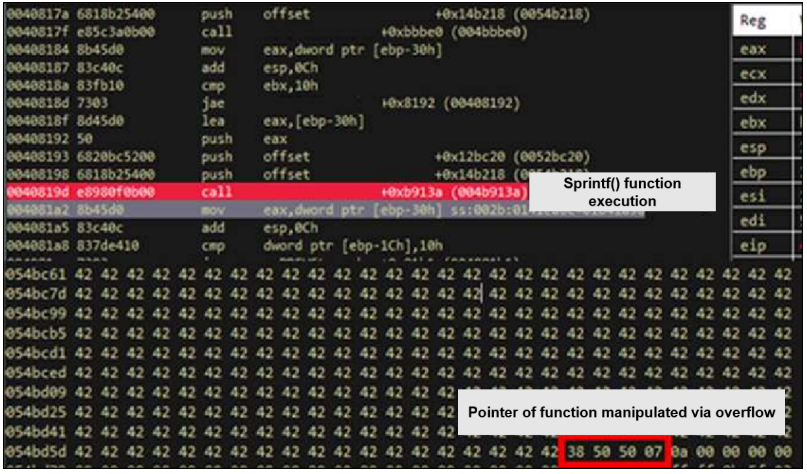
Therefore, it becomes possible to write a larger amount of data to the buffer than the
originally designated buffer size (512 bytes), and the execution flow of the program can be
modified using this. To attack the vulnerability, the function pointer stored in a specific
memory location is manipulated into a memory address that can go to the desired code. In
figure below, the function pointer is stored at 0x54bd70 and manipulated to 0x07505038 so
that the desired code can be executed. The attacker's shellcode is stored at 0x07505038
using the heap spray attack technique3). In other words, if a user of the application accesses
the manipulated web page in which the code for inserting data into the vulnerable function is
inserted as shown below, the malicious code can be executed. In addition, in the case of
Non-ActiveX that communicates with the web server, an attacker can send an attack packet
(exploiting a vulnerable function) to perform an attack without user interaction even if the
attacker only knows the user's IP.
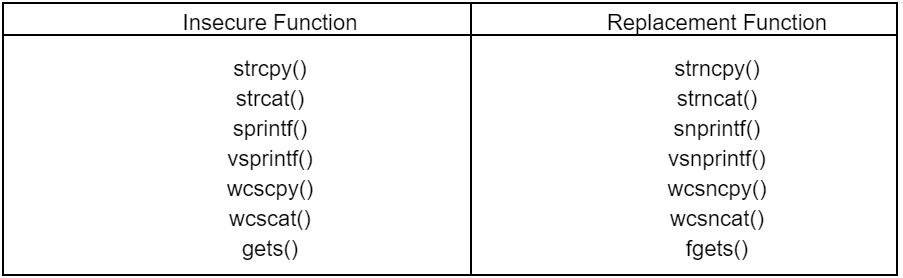
How to Fix Vulnerabilities
When developing an application, substitute a function that is not safe for overflow
vulnerabilities like strcpy() with a safe function like strncpy() and use it.
Be sure to set bounds or checks so that memory is not read or stored beyond the bounds of the memory buffer. When using a memory buffer in a program, set an appropriate buffer size and control reading or writing within the set range of memory.

Apply memory protection techniques such as Non-executable Stack, StackGuard, and ASLR to make it difficult for an attacker to successfully attack even if a vulnerable function exists.
※ It can be set in the compiler option (/DYNAMICBASE, /NXCOMPAT, etc.)