
SUMMARY
VPN has various methods such as remote access from site-to-site. However, from the viewpoint of an attacker, it is an attractive hacking object that can penetrate into an important path to enter an internal network only if a VPN is penetrated. Actually, site: vpn. * Com is a lot of domestic sites starting with vpn can be searched, but telecommuting, telemedicine and so on, many companies and organizations have many VPN service, It seems to be getting higher and higher. I have recently summarized some of the issues that need to be taken into consideration while diagnosing VPN mock hacking, which is one of the mock hacking diagnoses requested by clients. I would like to have a lot of reference when there is a request for VPN diagnosis in other projects.
The VPN connection configuration can be summarized as follows.
| Client -> VPN G / W -> Internal N / W |
The threats and attack points for the above VPN connection configuration can be set as follows.
|
a) client b) communication protocol c) VPN G / W d) Internal N / W
|
The major diagnosis contents and diagnostic results for each of the simulation hacking points described above are as follows.
CLIENT
1) VPN user authentication account guessing attack In addition to the account and password, the VPN service requires additional authentication information in a separate channel such as OTP. However, since the additional cost is required, the VPN service using the lowest level authentication method, It is a reality that there are more places to authenticate.
The client of this project had an internal issue, and the user account was operated in conjunction with AD. Guessing or brute force attacks were impossible because the password of AD account was using complexity and length restriction policy with strong security policy.
In addition, the client company has provided a control device that can detect the attack with some client connection attempt information, but since it is a simple method to detect the attack with the client's information, various methods have been found to bypass it .
IP and other information sent by the client can be manipulated as much as possible.
2) Attack Using VPN Client Module Vulnerability In VPN G / W, there is a program that is downloaded and installed on the client. Since the target device of this project is Juniper VPN, a program called network connect is installed in the VPN client as an ActiveX controller In addition, various exe and dll files are installed.
A simple analysis of this network conncetion program with Process Explorer shows that after running dsNetworkConnection.exe and running Juniper Setupclient.exe, dsHostCheckerSetup.exe will change the configuration of the PC, including changing the host file settings.
This process rewrites the files in the Juniper Networks directory. After analyzing some of the ini files that are easily accessible to the attacker, the config.ini and versioninfo.ini files can be modified However, there is a vulnerability that can overwrite the contents of the file because it has write access to the directory.
Although overwriting these files does not directly provide a reason for acquiring any privilege, it can be used as a vulnerability that can easily bypass control if the server side is using the value of a variable such as current_user or Current_Domain .
3) Attack using other malicious codes of VPN Client If the VPN Client successfully authenticates, the same access privilege is given to the PC located on the internal network. Therefore, the security of VPN Client is emphasized in most VPN security guides have.
In particular, PCs located outside the company's internal PCs, such as telecommuting or telemedicine, are more likely to be infected with malicious code such as viruses, so antivirus, anti-malware, patches Etc. should be basically secured.
In this project, we have excluded from the scope of diagnosis because there are so many different scenarios in this project. However, it was confirmed that various attacks were possible by testing and installing malicious code separately from this project.
COMMUNICATION PROTOCOL
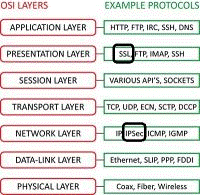
The VPN communication protocol is largely divided into SSL and IPSec. A simple way to distinguish between them is to scan the VPN G / W to see if 500 ports used by the IKE protocol are detected, and if the 443 port is detected, (Windows Server VPNs PPTP and L2TP VPN will detect 1723 and 1701 ports.)
(From the OSI 7 Layer perspective, IPSec belongs to the third layer, Network Layer, and SSL is the sixth layer Because it belongs to the Presentation Layer, the attack method varies greatly according to the protocol.) Since the
client's VPN was SSL method, we confirmed the Heartbleed and Poodle vulnerability with known SSL protocol vulnerability.
The way to check is confirmed by using nmap script, and by checking other methods to confirm the scanning result of nmap again, it is confirmed that Heartbleed is not vulnerable but vulnerable to poodle attack.
However, since the poodle vulnerability is an attack method that is difficult to attack while repeatedly coding, it is reported as a vulnerability that should be kept in mind.
VPN G / W
As with most network devices, VPN G / W usually provides a variety of services to access the device itself. Telnet and ssh services are basically provided as web services for management. If these services are exposed to arbitrary majority, stronger security measures should be applied since they can lose the authority to VPN G / W itself . This project focused on VPN G / W access control, and several important vulnerabilities were found.
1) VPN G / W XSS Vulnerability The Juniper SSL VPN G / W, which is a target device, achieves high market share while XSS vulnerabilities are well known. These vulnerabilities are registered with CVE and CAN.
Most of the known XSS vulnerabilities listed below exist, but fail to do direct attacks because SSL tunneling is a prerequisite for using XSS.
Therefore, this XSS vulnerability reported a list of identified XSS vulnerabilities as it could directly lead to an effective attack when combined with SSL vulnerabilities such as Heartbleed or poodle.
| https://target.com/dana-na/auth/url_default/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_3/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_15/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_22/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_23/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_24/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_5/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_0/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_4/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/auth/url_12/welcome.cgi?p=logout&c=37&u= </ script> <script> alert (1) </ script> https://target.com/dana-na/meeting/meeting_testresult.cgi?redir=/dana-na/meeting/login_meeting.cgi"><script>alert(999)</script>&java=1 https://target.com/dana/fb/smb/rd.cgi?si= "); alert (999); </ script> https://target.com/dana/fb/smb/wu.cgi?dir=foo "> <script> alert (999); </ script> |
2) VPN G / W Web Interface Exposure Vulnerability As with most network devices, the target VPN G / W was also provided with IVE Web Service, which can log in to the device, and /dana-na/auth/url_22/welcome.cgi and / I found dana-na / auth / url_admin / welcome.cgi.
As a result of testing two cgi, the former welcome.cgi is linked with the normal user AD account, and the latter welcome.cgi is the cgi for the device management and it is not connected with the AD account.
Especially, welcome.cgi for equipment management was more dangerous because there were no additional authentication factors such as ID / PWD and OPT. The diagnosis of welcome.cgi for this administration performed only a few guessing tests and reported the risk.
In addition, there were several web interfaces such as meeting login of Junos Pulse Collaboration Suite, but only simple guessing test was performed and the contents were reported.
Such a web interface is a high-risk vulnerability that can take over the authority of the VPN G / W device itself, so careful management will be required.
3) Bash shell Vulnerability Juniper SSL VPN is a type of network equipment that is based on FreeBSD, which is the operating system of JUNOS. Therefore, it may be vulnerable to bash shell bug.
In Juniper Network, only Junos Space and JSA Seriese are known to be vulnerable, but the posting was still under verification, and if there is a bash shell vulnerability, it can be an important step to gain the authority of VPN G / W. We identified a bash shell vulnerability known as seven CVEs.
A known way to check for a known bash bug vulnerability is to directly login to the target device by shell login. However, this project is an environment to diagnose by blackbox test method externally. We confirmed the vulnerability by inserting shell code in header value like User-Agent starting with magic string value () {:;};
However, it has been confirmed that there is no bash shell vulnerability in this device.
4) Other Vulnerabilities In addition to the functions provided by JUNOS's IVE, some weaknesses were found in the HTML source of the Web service, which was partially developed by the client's needs .
These vulnerabilities do not provide a direct clue to attack, but they should be removed because they provide the attacker with various information about the state of the target system.
INTERNAL N / W
The purpose of the project vulnerability diagnosis was to revalidate existing vulnerabilities after security measures, so several important vulnerabilities have been found after logging in as a VPN client with a test account.
1) Spoofing other user accounts with VPN Session Modulation We found a vulnerability that could steal other users by modifying the cookie values of other users on the same network while logged in to the VPN using the test account granted for this test , IVE itself is a vulnerability, and Juniper Networks has provided information about the vulnerability to Juniper Networks and asked to confirm it.
Although this vulnerability is a vulnerability that can succeed on the assumption of environmental conditions that can steal other users in the same network, it can be evaluated as a high-risk vulnerability because it is a vulnerability that can be achieved by modifying only one cookie value of the other user have.
In addition, if the EP account is accessed differently after logging in as a VPN, the customer is exposed to the risk of being abused as a method of bypassing the control because the control policy for blocking the EP login is applied .
2) Providing excessive routing information to the VPN Client For the test, we logged in to the VPN using the test account and checked the routing table with the client receiving the internal IP. As a result, we confirmed that over 300 routing tables were downloaded I was able to.
This routing table can be checked with the netstat command, which is a general command of Windows, but it can also be checked by the network connection program, a Juniper VPN client.
As a result of analyzing the routing table roughly, the routing table of the B class as well as the C class was allowed to be entirely plural.
In this network access control structure, in order to control access to the VPN client, each server farm or server needs to be structurally protected against access control.
Normally, a VPN client that is normally logged in can be thought of as a trusted user, but access control should be performed on the assumption that the user is significantly less reliable than a local user of a company or organization.
3) Acquisition of internal network system authority and bypassing access control As mentioned above, it is possible to connect to various systems operating in the internal network without difficulty by using the overloaded routing table.
The web service provided to the VPN Client is naturally accessible and the vulnerability of the web service can be exploited by the VPN Client as well as accessing some DB servers.
We could obtain DBMS authority by using vulnerability of DB server, acquire OS privilege using utility of DBMS, and acquire privilege to other peripheral system controlled by using acquired OS privilege
CONCLUSION
Here are some lessons from this VPN mock hacking diagnostic example:
1) VPNs from the attacker's point of view can be a very attractive target to enter an enterprise or organization's internal network.
2) Since VPN G / W is an important boundary between an internal network with a high reliability and an external network with a low reliability, security design and control should be done with a defense in depth strategy. )
3) VPN Client should be designed with security, such as authentication and authorization, access control, logging, and backup of network and system, assuming that it is untrusted user. (It will be added as VPN security guide later)