CLIENT
The Ministry of Information and Communication of Moldova
NATIONAL ICT STATUS
The Republic of Moldova, which is a developing country in Eastern Europe, is centered on the Ministry of Information and Communication (MITC), the Ministry of Information Technology and Communication (MITC), which establishes a national e-government plan called e-Moldova and invests about 8% Digital Moldova 2020 ", a medium- to long-term ICT strategy from 2014 to 2020, is being set up and promoted in 2011. The main contents of "Digital Moldova 2020" composed of 4 pillar are as follows.
- The Pillar the I: Informational Infrastructure Development and Improving Access for the Everyone
- The Pillar II:, Creating favorable the Conditions for Is the Development and the Use of National Digital Content
- The Pillar III: Increasing Is the Digital Literacy Degree, Is the Digital Skills and Digital the Inclusion Development
- The Pillar IV: Establishing conditions for increasing digital space security and trust
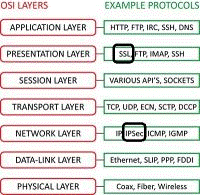
NATIONAL CYBER SECURITY STRATEGY STATUS
In accordance with Pilar IV establishing conditions for digital space security and trust of "Digital Moldova 2020," MTIC, the main ministry, refers to the Cyber Security Strategy of the European Union and the International Standard Guidelines, and adopts the National Cyber Security Program as a mid- It was under development.
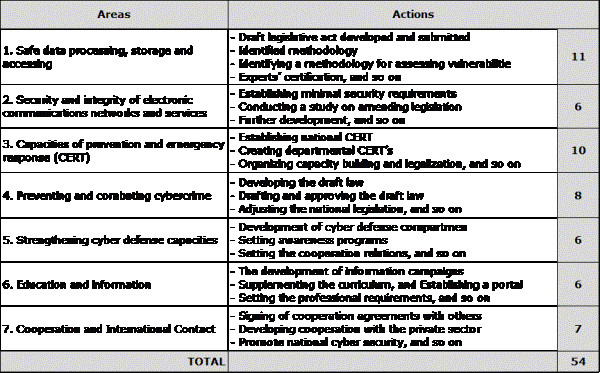
During the project, the National Cyber Security Program has been revised several times. In the final draft, it consists of 7 areas and 54 detailed actions.
PROJECT SCOPE
The objective of this project is to materialize the National Cyber Security Program under development, which MTIC collects the requirements of relevant organizations and stakeholders in Moldova and presents 11 requirements as requirements of this project. The details were identified and the redundancy and the relation with the requirements were grasped and compressed into four tasks. Two tasks were added at the request of Deputy Minister in the middle of the project, and the task of this project was defined as 6 tasks in total.
- Task-Amperes: Methodology Recommendations for Role and Responsibilities Definition
- Task-B: Approximate Budgets Estimation for Each Call the Action
- Task-C: Introduction The of Is the International Standard and Korean Government Case
- Task-D: Some Improvement Suggestions for Is the the Current Cyber Security program
- Task-X01: Penetration test for Government network
- Task-X10: Penetration test for a Critical Information Service
PROJECT SCHEDULE
The project period was contracted for a total of 3 months. When each task started, related data were collected and requested additional data or interviewed. Since we conducted the review, we proceeded on a tight schedule to complete one task in average two weeks.
PROJECT PERFORMANCE RESULT
Task-A: Methodology Recommendations for Role and Responsibilities Definition
The purpose of Task-A is to investigate and recommend methodologies to define the responsibilities of the 54 actions that make up the National Cyber Security Program under development. Since the National Cyber Security Program is a medium- and long-term cyber security promotion plan for the state of Moldova, a total of 26 related organizations exist as stakeholders, so we have defined the roles and responsibilities of 54 action plans using the methodology widely used as International Standard .
The RACI methodology, which is widely used in the global context, is introduced considering the time and resources of this project, and how to use this methodology. Using this methodology, the roles and responsibilities for the 54 action plans of the National Cyber Security Program ) And submitted it as an output.
Task-B: Approximate Budgets Estimation for each action
The purpose of Task-B is to estimate the approximate budget cost of the 54 actions that make up the National Cyber Security Program. MTIC, which is in charge of the development of the National Cyber Security Program, is an essential element for planning the annual and total budget for each action plan, approving it internally, and approving the budget.
In order to carry out this task, we first grasped the details and purpose of the action plan consisting of 54, and divided each action plan into three types (Consultation Project, System Integration Project, and Self-Execution Project). The reason for dividing them into three types is that the corresponding action plan has different calculation criteria.
For example, in the case of an action that creates a standardized vulnerability diagnostic methodology of Critical Information Infrastructure, it will be calculated as M / M (Man Month) to be put into a professional consultant. In case of an Action to build a National CSIRT, Network equipment and the like must be calculated.
In addition, in case of establishing cooperation relationship for cyber infringement information exchange with neighboring countries, it is classified as a self-project which does not require extra budget because it can be covered by self-operation fee.
After classifying 54 Action Plans into 3 types, we calculated the budget according to each budget for each Action and calculated each year, period and total budget.
In particular, the budget has been modified so that the basic data can be changed in consideration of the characteristics of developing countries, so that it can be automatically reflected in the budget for each action.
Task-C: Introduction of the International standard and Korean government case
National Cyber Security Program, which consists of 54 actions, is an entity that is responsible for sharing ownership between 26 agencies and related departments. Therefore, it is necessary to define each Action in detail The case of the international standard and other advanced countries including Korea becomes important reference materials.
Therefore, the purpose of Task-C is to investigate and map the International Standard or Model for each action, the cases of Korea and other developed countries.
In the case of Korea, the content and standardization of the ISMS and PIMS system, the CPO of the information and communication service and the financial corporation, the mandatory holding of the CISO, We surveyed related data on domestic professional qualification systems such as information security experts and industrial security experts, and carried out Englishization work and mapping.
Examples of other countries such as NIST in the United States, European ENISA, NATO CCDCOE, TF-CSIRT, FIRST, and CERT / CC are mapped to Others,
One of the websites that I learned while doing this project was that there was an English version statutory inquiry function on the website of the statutory inspection website in Korea. (Reference:http://www.law.go.kr/LSW/engLsSc.do?menuId=0&subMenu=5&query= ) When I was working on projects in developing countries such as Colom, Bar and Rwanda, Respectively.
Task-D: Some improvement suggestions for the current cyber security program A
few years ago, a guide to establishing the National Cyber Security Strategy was developed and published by ITU, ENISA and NATO CCDCOE in Europe, There are a lot of references available. In the case of the European Union Agency, ENISA, we collect, research and publish national cyber security strategies for countries around the world including the European Union countries every year. We also provide and support various programs such as the CERT Capability Building Program.
In fact, the use of such published standards or program materials has become more than enough to establish national cyber security strategies. It is very easy to duplicate the national cyber strategy of other countries in a similar environment, and there are detailed materials that can be modified and used according to the local environment. Moldova also developed an initial National Cyber Security Program in this way, so it was necessary to conduct an objective review on whether there was a missing strategy or action.
Therefore, the purpose of Task-D is to present an overall improvement plan through evaluation of National Cyber Security Program under development.
In order for objective performance of this task to be objective, an objective evaluation or inspection standard of a reputable institution was required, it was first necessary to consider the situation of Moldova in accordance with European Union standards, We made a checklist based on the "Guidebook on National Cyber Security Strategies" and conducted GAP analysis with the current Moldova national cyber security program. As a result, we obtained 20 improvement points. Respectively.
Especially, considering the economic situation in Moldova where the average initial college graduate is just over $ 100, there are some improvement measures such as the industrial security articles of Korea which are not mentioned in standard guide such as ITU, ENISA, NATO CCDCOE It emphasized that the introduction of domestic professional qualification systems and certification systems such as ISMS, PIMS, and PIPL have high economic efficiency and effectiveness.
Task-X01: Penetration test for Government network, Task-X10: Penetration test for a Critical Information Service
At the request of the MIC's Deputy Chief, we conducted a mock-up hacking diagnosis of the Moldovan government's network and Critical Information Security Service, What vulnerabilities should be supplemented, and what parts should be supplemented in the future.
As a result of two simulated hacking diagnoses, all of them got the root privilege of the target system, and there was a request from MTIC to omit some contents from the official report.
The protection measures against the result of the mock hacking diagnosis are divided into short term and long term protection measures. In particular, Secure SDLC for e-government projects that are continuously developed and built showed a high interest, SW security vulnerability diagnosis and emphasized the necessity of institutional introduction.