* There are many purposes to hide your IP
- When Google pulled out of China, there were a lot of Chinese who used public VPNs to bypass blocking
- There is a situation where you have to hide your IP inevitably in order to execute Real PT composed of Red Team
- It may be used to bypass the blocked IP itself while diagnosing security vulnerabilities
- It is also used to test a different source IP after developing a simple security system.
- You can use it to deceive your physical location like the Fake GPS of the popular Pokemon game
(Now in CN, the gun is down and the attack is going to attack. We are struggling with each other to fight the house and boss or cattle.
* There are many ways to hide your IP
- If your destination is the Internet rather than the internal network, there are a number of ways and some companies offer it commercially, but the important thing is to choose which method to use for your purpose.
- How to use Open or Private Proxy Server
- How to use Cloud Server or Open Shell Server
- How to use Open or Private VPN
* This is a way to use Open VPN
- It is a method of using a VPN which can guarantee relatively safety among the methods of hiding self IP.
- VPN Gate, which updates the list of about 6,000 Public VPN Proxy Servers by volunteers from around the world.
- There is also a way to access and use this Public VPN Realy Server directly through the configuration (see http://www.vpngate.net/en/)
- As you can see from the source, vpngate provides api so that you can easily get VPN Relay Server information.
- autovpn uses this api and was made with Google's development language go, but I have revised it a little (see source below)
(Well ... so, you need to have golang and openvpn installed)
* The modified source code (autovpn.go) is as follows
// autovpn.go
//
package main
import (
"bufio"
"encoding/base64"
"fmt"
"io/ioutil"
"net/http"
"os"
"os/exec"
"os/signal"
"strings"
"syscall"
)
func check(e error) {
if e != nil {
panic(e)
}
}
func main() {
chosenCountry := "US"
if len(os.Args) > 1 && len(os.Args[1]) == 2 {
chosenCountry = os.Args[1]
}
URL := "http://www.vpngate.net/api/iphone/"
fmt.Printf("=> getting server list\n")
response, err := http.Get(URL)
check(err)
defer response.Body.Close()
scanner := bufio.NewScanner(response.Body)
fmt.Printf("=> parsing response\n")
counter := 0
for scanner.Scan() {
if counter <= 1 {
counter++
continue
}
splits := strings.Split(scanner.Text(), ",")
if len(splits) < 15 {
break
}
hostname := splits[0]
country_long := splits[5]
country := splits[6]
conf, err := base64.StdEncoding.DecodeString(splits[14])
if err != nil || chosenCountry != country {
continue
}
fmt.Printf("=> writing config file\n")
err = ioutil.WriteFile("/tmp/openvpnconf", conf, 0664)
check(err)
fmt.Printf("=> lokking for %s(%s)...Server:%s\n", chosenCountry, country_long, hostname)
cmd := exec.Command("sudo", "openvpn", "/tmp/openvpnconf")
cmd.Stdout = os.Stdout
c := make(chan os.Signal, 2)
signal.Notify(c, os.Interrupt, syscall.SIGTERM)
go func() {
<-c
cmd.Process.Kill()
}()
cmd.Start()
cmd.Wait()
fmt.Printf("=> try another VPN Server? (y/n) ")
var input string
fmt.Scanln(&input)
if strings.ToLower(input) == "n" {
os.Exit(0)
}
}
}
- First you need to install the necessary packages (pass if you already have them)
$ sudo apt-get install golang
$ sudo apt-get install openvpn
- Then compile the autovpn source you received
$ go build autovpn.go
- Now, execute the following (connect to the Public Domain Relay Server of the country domain received as a parameter)
$ ./autovpn TH <= Thailand
Screenshot of running autovpn before and after
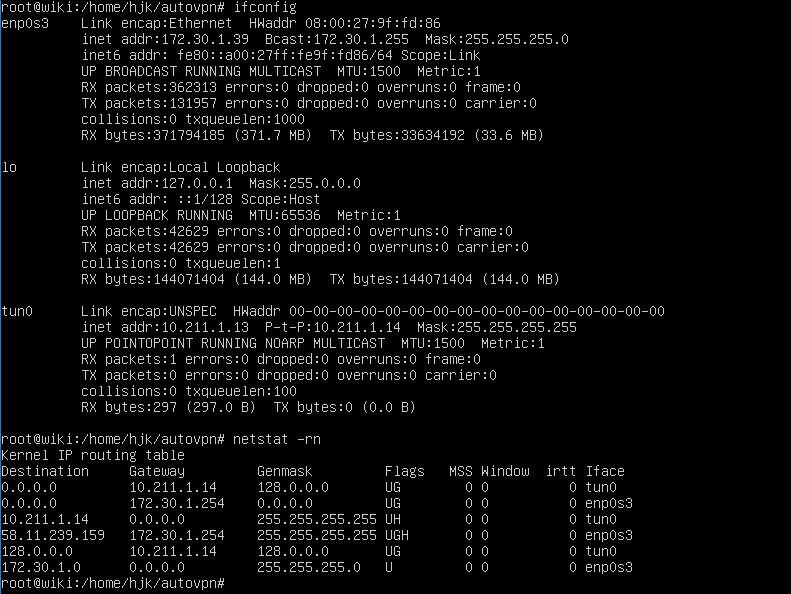
- Before running autovpn, there are only two network interfaces and routing tables.
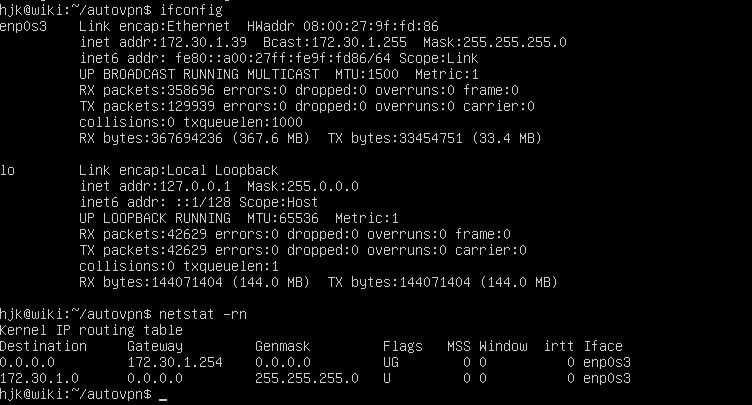
- After running autovpn, a NW interface named tun0 was added, and P2P Trunneling was created with the VPN Relay Server in Thailand which also set the routing table.