SECURITY VULNERABILITY TEST SERVICE
EXECUTIVE SUMMARY
Security vulnerabilities are found in most systems, such as acquired systems and developed systems, due to the lack of patches, lack of security settings, lack of security coding, and lack of change management.
Therefore, most of the international standards or certification standards for security management system specifies periodic security vulnerability check as one of the essential requirements.
Once the Security Vulnerability Test is completed, You will achieve the following goals:
ㆍIdentify where, and what information systems are present through information assets surveys
ㆍRecognizing how many security vulnerabilities exist in which information systems
ㆍAnalyzing how dangerous a vulnerability is, and which vulnerability is important
ㆍSelecting various methods to remedy found security vulnerabilities
ㆍEnhancement of self-competence for periodic security vulnerability checks
※ Related international standards and regulations
ㆍISO/IEC 27002:2013 : A12.6 Technical Vulnerability Management
ㆍPCI-DSS v3.2 Requirement 11.2 : External and Internal Network Vulnerability Scans
ㆍEU GDPR Regulation: Article 32 Security of Processing
ㆍRwanda RURA Regulation: Article 21 Vulnerability Assessment (on all the plane twice a year)
SERVICE STRATEGY
In order to achieve the ultimate goal of security vulnerability review, Vulnerability Management Lifecycle, which identifies existing information assets, prioritizes priorities, identifies existing vulnerabilities, analyzes them, measures them, It is necessary to consider all activities from the perspective.
A. Providing Service from Vulnerability Lifecycle
- Providing All Activities from Technical to Managerial parts of Vulnerability Management Lifecycle
- Providing related managerial policies, procedure, and standards of Vulnerability Management System
B. Accurate Test using the Latest Vulnerability Database and Tools
- Testing the Security Vulnerability Using the Updated Database with All the Latest Vulnerability Information
- Using Globally Verified Dedicated Vulnerability Testing Tool by Each Type of the System
C. Providing Professional Technical Assistance Service
- Professional Training for Practitioners to Build Self-vulnerability Test Capability
METHODOLOGY
Vulnerability Testing consists of 5 phases from Asset Identify to Treatment and Planning. Depending on the Target of Vulnerability Test, many testing techniques are used in the detailed steps of each phase.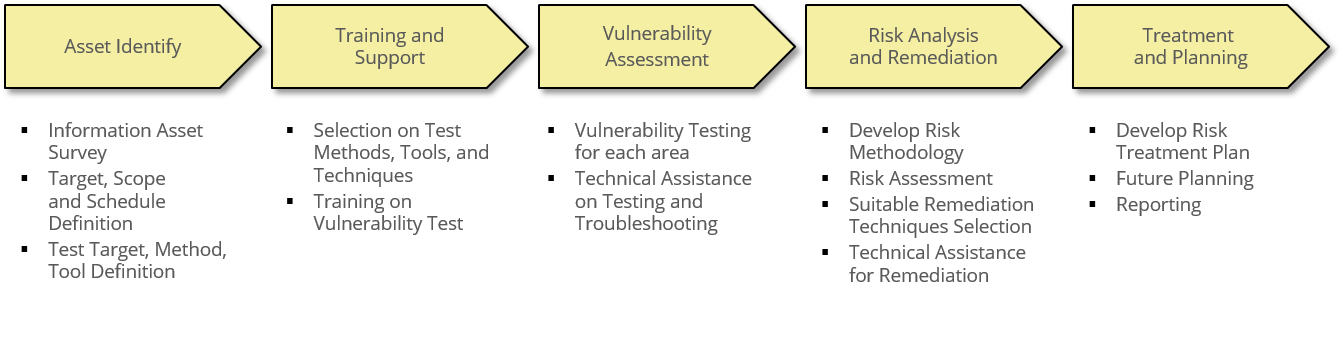
PROJECT CASE
Client :
SK Group Company
Vulnerability Test Type:
Web Application/Mobile APP Source Code Review
Testing target:
Internal and external Web applications and Mobile APP on operating(by automated tools and manual test)
Testing Techniques:
- Dedicated automatic testing tools to match the type of information system
- Manual testing of professional consultants
Testing Results:
Many vulnerabilities related to patches were found in security vulnerability testing using automation tools, but most security vulnerabilities related to business logic were found through manual testing rather than tools.
Peculiar Things
- Cross-checking with dynamic analysis of professional engineers based on static analysis results using automated testing tools
- In the dynamic analysis of expert engineers, more security vulnerabilities with higher severity has been found.