These are the research and development outcomes produced by the WiKi Security R&D Center. Each result has standalone value as an individual product or solution, and can also generate additional value through collaborative development by integrating with related systems from other companies.
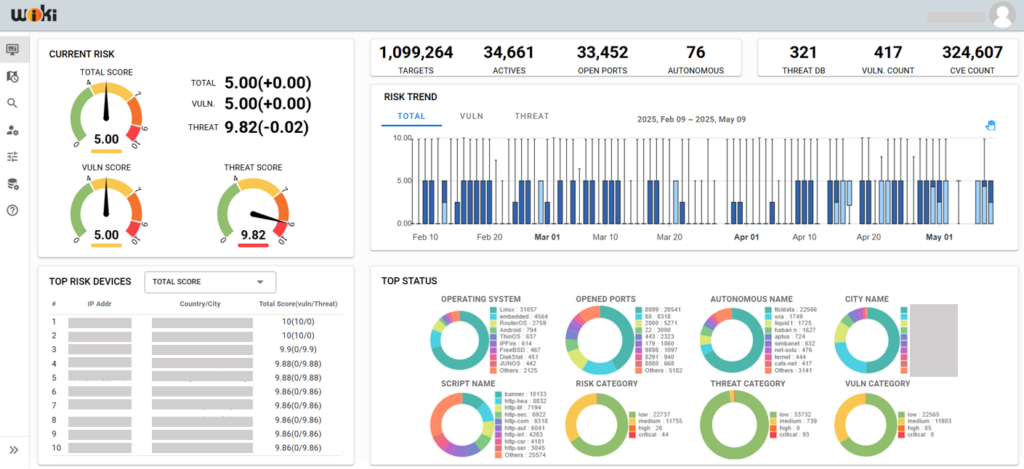
WiKi-RAV(Reconnaissance Aerial Vehicles)
Just as Europe has Shodan.io, the United States has Censys.io, and China has Zoomeye.org, Korea has WiKi-RAV.
– Product Introduction Video (EN): WiKi-RAV Product Introduction Video
– Collection of Instructional Videos (EN): WiKi-RAV Instructional Video
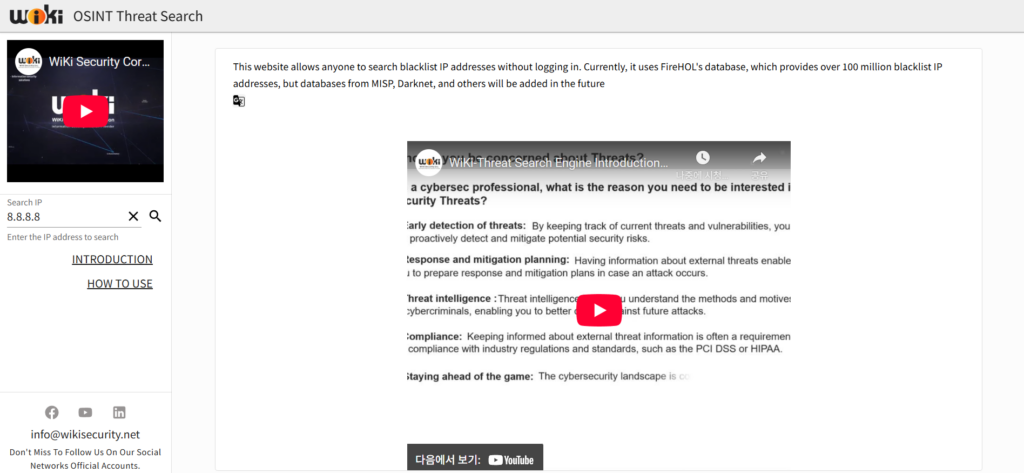
WiKi-THREAT
Our R&D Center has developed and published a simple web platform that enables users to search for malicious IP addresses based on FireHOL’s Blacklist IP, Blocklist IP, and Reputation IP databases.
The database is continuously updated—on a minute-level or weekly basis—with over 100 million blacklist IPs sourced from more than 80 global security organizations, including US-CERT, IBM X-Force Exchange, and AlienVault, providing a comprehensive and reliable IP threat lookup service.
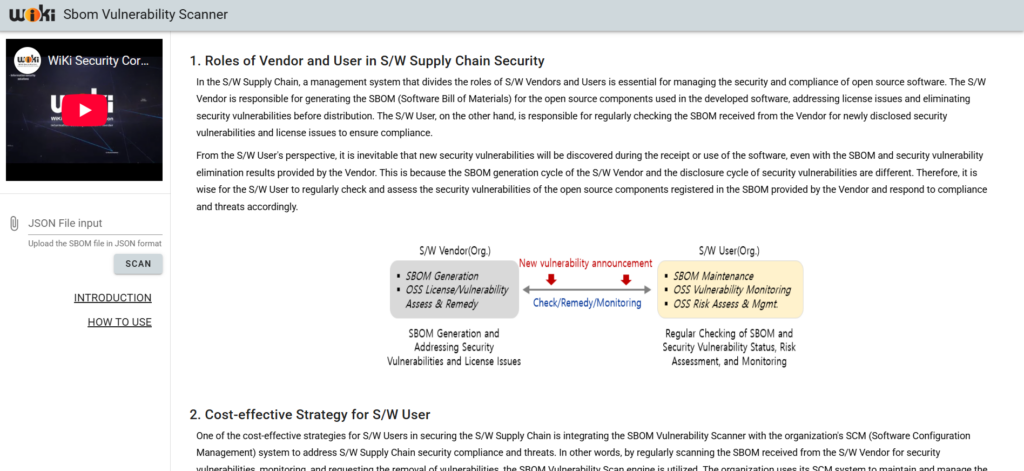
WiKi-SBOMVUL
The creation of an SBOM (Software Bill of Materials), a core element of software supply chain security, is a critical responsibility that must be owned by the software manufacturer (developer). However, software consumers (operators) must continuously monitor newly disclosed security vulnerabilities against the SBOM they receive and request security patches from the manufacturer when necessary.
From this perspective, we are releasing an SBOM vulnerability scanning website that can be used for SBOM management and security vulnerability analysis. This website is available to anyone, and by uploading an SBOM file in JSON format, users can scan for all known security vulnerabilities and view the results through a simple and intuitive interface.
WiKi-WS(Web Vulnerability Scanner)
Most organizations operate policies that require regular security assessments of their web applications. This platform was developed to support those recurring security activities. Unlike traditional web vulnerability scanners, it offers differentiated features such as malware detection within web content and cryptojacking analysis, with additional capabilities continuously being added.
The website is available to registered users, and access is granted through a verification process that confirms the target website is under the user’s administrative control.

