- Certification Consulting
- Compliance Consulting
- Penetration Test
- Vulnerability Testing
- System Implementation
ISO/IEC 27001 CERTIFICATION READINESS CONSULTING
EXECUTIVE SUMMARY
As concerns over information security continue to increase, a growing number of business partners, customers, regulators, and other stakeholders require the organizations they do business with to demonstrate that the organizations have a sound information security management system (ISMS) in place. The most widely recognized data security standard is ISO/IEC 27001. Increasingly, having ISO/IEC 27001 certification is essential for doing business with many leading enterprises globally.
Our proven methodology over many years of projects will save your team months of effort in implementing ISO/IEC 27001 and making a workable plan to achieve it. And our experts guides you through all things needed to come into full compliance with ISO/IEC 27001.
Once this project is completed, You will achieve the following goals:
ㆍIdentification and risk assessment of all information assets
ㆍSecurity Vulnerability Test and Penetration Test for Information Systems
ㆍISMS Assessment and Implementation in accordance with the ISO/IEC 27001 requirements
ㆍISO/IEC 27001 Certification Audit of Global Certification Body (optional)
SERVICE STRATEGY
Our strategies to achieve successful ISO / IEC 27001 certification based on many years of experience and know-how is as follows.
A. Professional Consultant T / F Team Composition
– Consists of ISO / IEC 27001 Lead Auditor, Auditor qualification consultant
– Many years of experienced staff in ISO / IEC 27001 ISMS Assessment and Implementation
– Experts of security vulnerabilities and Penetration Testing technicians in various industries
B. Integration with Global Certification Body
– Proposal including Certification Body Auditing to overcome Initial Audit failover
– Certification acquired in a short period of time (minimum 3 months)
C. Know-how and technology transfer in project process
– Establishing consensus with stakeholders through training on ISO / IEC 27001 certification
– Technical transfer of technical security including security vulnerability testing
METHODOLOGY
The consulting methodology consists of 4 phases from Understanding to Certification Support. Depending on the scope of project, there are a little bit deference tasks and steps of each phase.
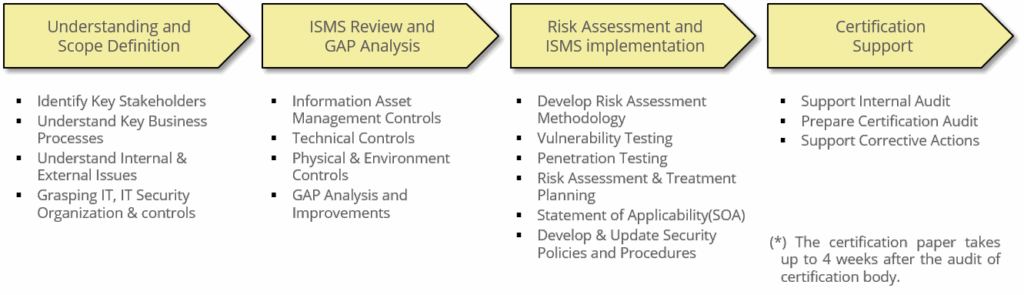
※ Deliverables
Scope Statement, GAP Analysis, Information Asset Inventory, Penetration Testing Report, Vulnerability Testing Report, Risk Assessment Methodology, Risk Treatment Plan, Internal Audit Plan & Results, Statement of Applicability(SOA), Information Security Policies & Procedures, ISO/IEC 27001 Training Materials, Corrective Plan, etc.
CERTIFICATION PROJECTS ACHIEVEMENTS
There are many clients who have obtained certificates through our consulting services. And our clients are distributed in various industries including financial companies, manufacturing companies and telecommunication companies. The most clients also usually use our consulting services to prepare for the annual surveillance audit after obtaining the certificate.
| In 2018, KT Rwanda Networks ISO/IEC 27001 Certification Consulting — KT, Telecom(Overseaes) ’18 K-ISMS Certification Operation Consulting — SK Onestore, SK Group Company In 2017, ’17 Vulnerability Analysis / Evaluation Consulting — Shinhan Investment Corporation, Shinhan Financial Group ‘17 K-ISMS Certification Operation Consulting — Shinhan Investment Corporation, SK Group Company K-ISMS Certification Surveillance Consulting — Seoul ST. Mary’s Hospital, Airline/Medical K-PIMS Certification Consulting — KOEN Co., Ltd., Public/Administration ISO/IEC 27001 Initial Certification Readiness Consulting — NHN Entertainment Corporation, Game Company In 2016, ’16 K-ISMS Certification Surveillance Consulting — SK Onestore, SK Group Company ’16 Vulnerability Analysis/Evaluation and Certification Consulting — Shinhan Investment Corporation, Shinhan Financial Group ’16 Daelim Corporation K-ISMS Certification Consulting — Daelim Corporation, Daelim Group Company ISO/IEC 27001 Certification Upgrade Consulting — Daewoo Engineering & Construction, Construction ’16 K-ISMS Certification Surveillance Consulting — SK Onestore, SK Group Company Website Vulnerability Testing (ISO/IEC 27001 Surveillance) — KTNET, Public Institutions Website & MoblieApp Vulnerability Testing (K-ISMS, K-PIMS) — SK Telink Co, Ltd., SK Group Company In 2015, Security Vulnerability Diagnosis (K-ISMS) — Hanwha General Insurance Co., Ltd., Financial Company ISO/IEC 27001 Certification Surveillance Consulting — Nanumlotto Inc., Manufacturer K-ISMS Certification Surveillance Consulting — KT, Telecom Company ISO/IEC 27001 Certification Surveillance Consulting — Daewoo Engineering & Construction, Manufacturer Infrastructure Security Testing (K-ISMS) — SKB, ISP Company In 2014, LG Electronics Overseas Corporation ISO27001, BS10012 Certification Consulting — LG Electronics, Group ’14 K-ISMS Certification and Infrastructure Testing Consulting — KT, Telecom Company K-ISMS Certification Consulting (including MobileApp Vulnerability Testing) — Tricycle, Financial Company Certification(ISO/IEC 27001, PCI-DSS, K-ISMS) and Reguler Vulnerability Testing — BC Card, Credit Card Company K-ISMS Certification Surveillance Consulting — Seoul Madical and Science Labortory, Healthcare In 2013, ISO/IEC 27001 Initial Certification Readiness Consulting — Daewoo Engineering & Construction, Online Shopping Mall K-ISMS Initial Certification & Technical Protection Consulting — YES24, ICT Company K-ISMS Consulting and Vulnerability Test — KTN, Telecom Company In 2012, ’12 Second half Vulnerability Test (ISO/IEC 27001, K-ISMS, PCI-DSS) — BC Card & Construction, Credit Card Company Korea Sports Promotion Foundation General Consulting (K-ISMS) — Korea Sports Promotion Foundation, Public Institutions Korearatings K-PIMS Certification Consulting — Korea Ratings, Financial Company Yonsei University Health System ISO/IEC 27001 Initial Certification Consulting — Yonsei University Health System, Healthcare Shinhan Aitas ISO/IEC 27001, BS10012 Initial Certification Consulting — Shinhan Aitas, Shinhan Financial Group In 2011, ISO/IEC 27001, K-PIMS Certification Readiness Consulting — Daesang Group, Daesang Group Company ISO/IEC 27001 and BS10012 Initial Certification Consulting — Shinhan Finace Invest, Shinhan Financial Group ISO/IEC 27001 and BS10012 Initial Certification Consulting — Shinhan life, Shinhan Financial Group ISO/IEC 27001 and BS10012 Initial Certification Consulting — Shinhan Capital, Shinhan Financial Group ISO/IEC 27001 and BS10012 Initial Certification Consulting — Jeju Bank, Shinhan Financial Group ISO/IEC 27001 and BS10012 Initial Certification Consulting — Shinhan BNP, Shinhan Financial Group ISO/IEC 27001 and BS10012 Initial Certification Consulting — Shinhan Credit information, Shinhan Financial Group ISO/IEC 27001 Certification Readiness Consulting — LG Inotek , LG Group Company |
PROJECT CASE-1
Client :
KT Rwanda Networks Ltd. (in Rwanda)
Project Scope : (completed)
All the necessary tasks for obtaining ISO/IEC 27001 certification (including certification audit of certification body)
Main Activities
– [SD] ISMS scope Definition
– [RM] Risk Assessment and Treatment (including Vulnerability Test and Penetration test)
– [IM] ISMS Implementation and Training
– [OE] Operation and Performance Evaluation
– [CS] Certification Support
Deliverables
– About 18 Mandatory Documents and Records
– About 20 non-mandatory Documents and Records
Peculiar Activities
– Educating and cooperating on ISMS review and improvements
– Training and sharing the testing role on Security Vulnerability Testing
– Know-how and technology transfer in all project process
PROJECT CASE-2
Client :
Daewoo Engineering & Construction (in Korea)
Project Scope : (completed)
All the necessary tasks and documents for obtaining ISO/IEC 27001 certification (including certification audit of certification body)
Certification Background :
ISO/IEC 27001 certificate is required to strengthen competitiveness of overseas construction business
Main History(with our consulting service)
– in 2013, Initial Certification
– in 2015, Surveillance Certification
– in 2016, Upgrade Certification(version 2013)
Peculiar Activities
– Minimize the scope of certification with “Operate of IT Infrastructure”
– Provided readiness consulting service for certification preparation every year after obtaining initial certification
– Provide technical assistance for security hardening against vulnerabilities found in the technical vulnerability test
REGULATORY COMPLIANCE READINESS CONSULTING
EXECUTIVE SUMMARY
Various regulations such as EU GDPR, PCI-DSS, SOX, HIPAA and SSAE are being applied to your company or organization at the government or industry level.
RURA, which operates under strong regulation at the government level, is a regulation that is applied to companies and institutions operating public facilities in Rwanda, and according to Law Nº 09/2013 of 01/03/2013, which governs RURA, it is applied as a mandatory to seven business areas as follows.
- Telecommunications, information technology, broadcasting and converging electronic technologies including the internet and any other audiovisual information and communication technology;
- Postal services;
- Renewable and non-renewable energy, industrial gases, pipelines and storage facilities;
- Water;
- Sanitation;
- Transport of persons and goods; and
- Other public utilities, if deemed necessary.
As most government-level regulations operate in general with strong penalties, a thorough preliminary preparation is required, since a large amount of penalty will be imposed if the RURA regulation is violated.
In addition, RURA’s information security regulations consist of detailed requirements that encompass not only technical security but also administrative security and physical security, therefore you have to organize and prepare an enterprise-wide T/F team.
Our consultants who have a thorough understanding of RURA regulations and have many years of experience in information security and various cases, can solve your troubles enough.
Once this project is completed, You will achieve the following goals:
- A good understanding of the information security experts for Audit Results
- Sufficient corrective action preparation and virtual simulation for Audit Results
- Implementing security document sets for managerial security required by Regulation
- Building cost effective security system for technological security required by Regulation
- Exhaustive advanced preparation for the all detailed requirements of Regulations
SERVICE STRATEGY
A. Professional Consultant T/F Team Composition
- Consists of consultants with years of experience dealing with various regulations in information security
- Consists of consultants who have a perfect understanding and experience for the regulation
- Consists of experts in the field of technical security for many years and experts in management and operational security
B. Rapid and Systematic Service Providing using by Pre-prepared Solution Portfolio
- Utilize pre-prepared standard templates and corrective actions for sectorial requirements such as Telecom, Broadcasting, and Information Technology
- Utilizes already prepared information security standard document set including appropriate information security policies, guidelines and procedures
- Use cost effective security solution portfolio already secured by technical security requirements of regulations
METHODOLOGY
The consulting methodology consists of 4 phases from Understanding to Certification Support. Depending on the scope of project, there are a little bit deference tasks and steps of each phase.
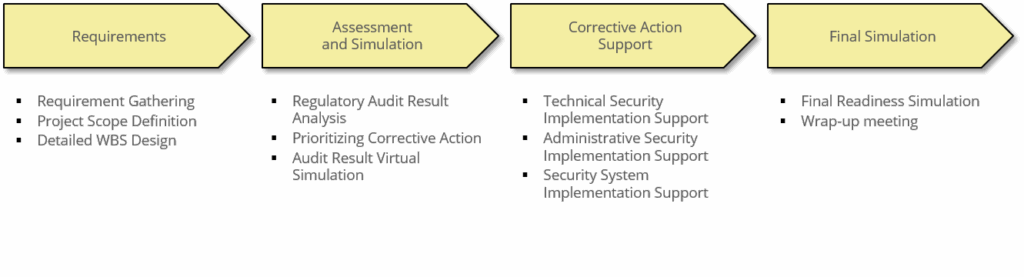
※ Deliverables
Corrective Action Plan, Phased Regulatory Compliance Virtual Simulation, Establish Security System Required by the Regulation (optional), Information Security Policies and Procedures required by Regulation, Information Security Education and Training required by Regulation
PROJECT CASE-TELECOM
Simulation of Compliance Status for RURA’s Telecom Network Security Requirements (15 Articles, 71 Requirements)
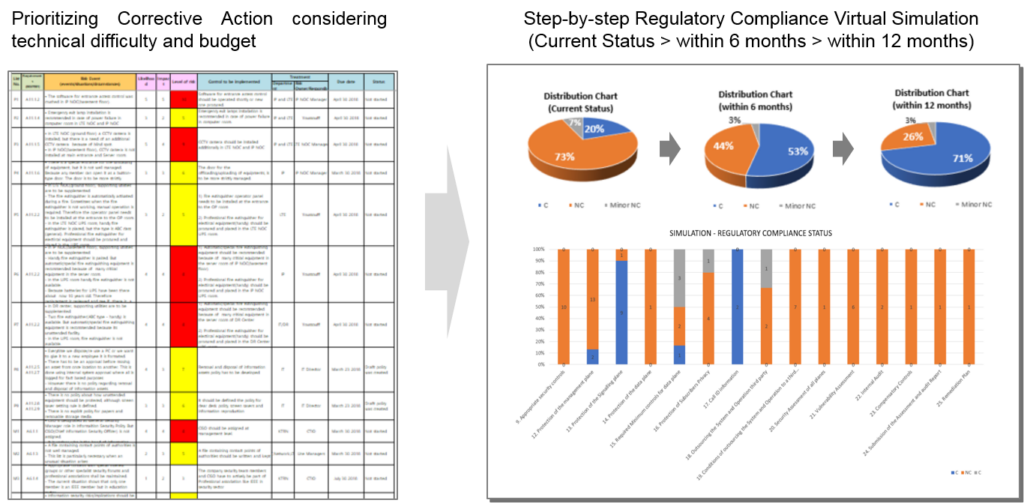
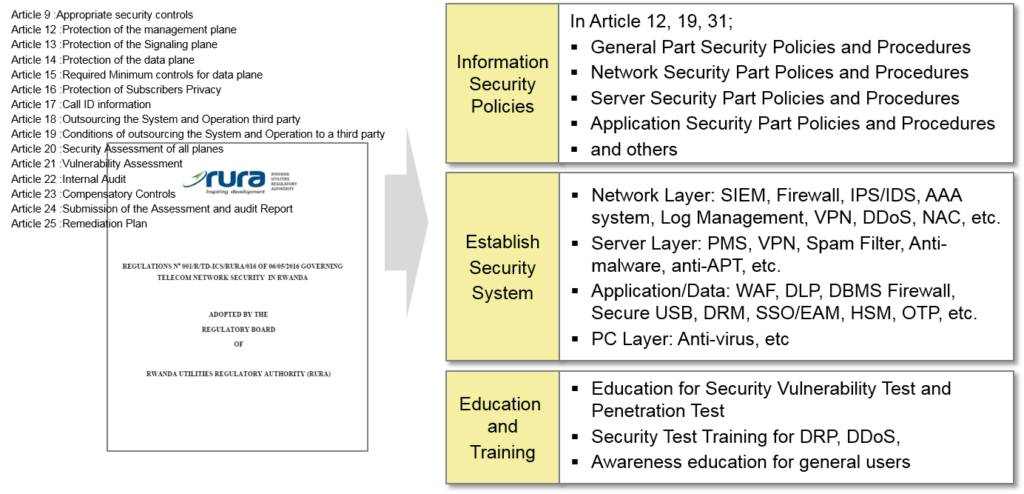
RURA regulatory requirements are largely divided into three categories, and service portfolios are provided according to requirements.
PENETRATION TEST SERVICE
EXECUTIVE SUMMARY
A penetration test, more commonly known as a ‘Pen Test’ or ‘Ethical Hacking’, is a simulated attack on a computer system with the intention of finding security weaknesses that could be exploited.
Penetration tests and vulnerability assessments we are providing offer an independent view of your existing security processes. It also help establish whether critical processes such as patching and configuration management have been followed correctly.
Once the Penetration Test project is completed, You will achieve the following goals:
- Compliance with relevant standards and regulations
- Identification of weak points requiring urgent action
- Planning of security treatment from the perspective of risk assessment (optional)
※ Related international standards and regulations
- ISO/IEC 27002:2013 : A12.6 Technical Vulnerability Management
- PCI-DSS Requirements: Requirement 11.3: Regularly test security systems and processes
- EU GDPR Regulation: Article 32 Security of Processing
- Rwanda RURA Regulation: Article 21 Vulnerability Assessment
SERVICE STRATEGY
In international standards such as ISO, ITU, USA NIST, EU ENISA and NATO CCD-COE, the type of network security threat is divided into internal threat, external threat, and privileged threat.
External Threat: occurs when someone outside your network creates a security threat to your network
Internal Threat: occurs when someone from inside your network creates a security threat to your network
Privileged Threat: occurs when someone from privileged inside your network creates a security threat to your network

METHODOLOGY
Penetration Testing consists of 5 phases from Discovery to Reporting. Depending on the Penetration Test Topic, many testing techniques are used in the detailed steps of each phase.
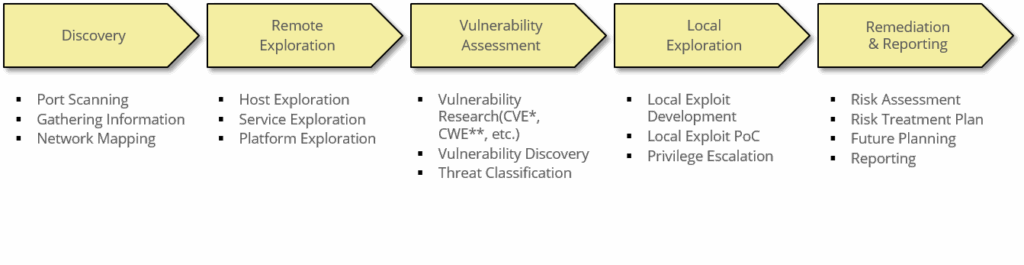
PROJECT CASE-1
Penetration Test Type :
External Penetration Test
Attack target :
A website for registering and managing SSN, Passport, etc. information of all citizens
Testing Results :
Remotely takeover Web administrator privileges and all DBMS Administrator’s privileges of the target system via the Internet
Attack Narrative :
Remotely takeover Web administrator privileges and all DBMS Administrator’s privileges of the target system via the Internet
a. Check opened TCP / 8580 with port scanning
b. Vulnerability Information search for ‘JBoss JMX Console'(TCP/8580)
c. Exploit Code Development (CVE-2010-0738)
d. Exploit Code injection, and remote login
e. Upload and execute Web shells(war file) with the Console Administrator privileges
f. Web Console and DBMS administrator’s authority takeover
Cause of attack success
– Open ‘JBoss JMX Console’ service port
– ‘JBoss JMX Console’ patch not available
PROJECT CASE-2
Penetration Test Type :
– Specific-theme Penetration Test
– Tested employee’s security awareness by randomly distributing CD with inserted malicious code in office
Attack target :
Any employee at headquarters
Testing Results :
Malicious code is inserted and randomly distributed CD is executed on its own PC, so that about 72% of employees infected with malicious code are collected in the logger server
Attack Narrative :
Remotely takeover Web administrator privileges and all DBMS Administrator’s privileges of the target system via the Internet
a. Consultation for test scenario with a person in charge of client
b. Malicious code development and safety testing with Excel file
c. Insert malicious code into the CD entitled “2016 Internal Personnel Assessment Results”
d. Developed Logger Server to collect infected PC information
e. Randomly distribute a specially-produced CD to the head office
f. Monitoring infection records on Logger server for 1 week
g. Collecting Infection PC Information from the Logger Server
h. Infection information analysis(by host, organizational unit) on the Logger Server
Cause of attack success
– Lack of information security awareness on treatment of removable media of employees
SECURITY VULNERABILITY TEST SERVICE
EXECUTIVE SUMMARY
Security vulnerabilities are found in most systems, such as acquired systems and developed systems, due to the lack of patches, lack of security settings, lack of security coding, and lack of change management.
Therefore, most of the international standards or certification standards for security management system specifies periodic security vulnerability check as one of the essential requirements.
Once the Security Vulnerability Test is completed, You will achieve the following goals:
- Identify where, and what information systems are present through information assets surveys
- Recognizing how many security vulnerabilities exist in which information systems
- Analyzing how dangerous a vulnerability is, and which vulnerability is important
- Selecting various methods to remedy found security vulnerabilities
- Enhancement of self-competence for periodic security vulnerability checks
※ Related international standards and regulations
- ISO/IEC 27002:2013 : A12.6 Technical Vulnerability Management
- PCI-DSS v3.2 Requirement 11.2 : External and Internal Network Vulnerability Scans
- EU GDPR Regulation: Article 32 Security of Processing
- Rwanda RURA Regulation: Article 21 Vulnerability Assessment (on all the plane twice a year)
SERVICE STRATEGY
In order to achieve the ultimate goal of security vulnerability review, Vulnerability Management Lifecycle, which identifies existing information assets, prioritizes priorities, identifies existing vulnerabilities, analyzes them, measures them, It is necessary to consider all activities from the perspective.
A. Providing Service from Vulnerability Lifecycle
– Providing All Activities from Technical to Managerial parts of Vulnerability Management Lifecycle
– Providing related managerial policies, procedure, and standards of Vulnerability Management System
B. Accurate Test using the Latest Vulnerability Database and Tools
– Testing the Security Vulnerability Using the Updated Database with All the Latest Vulnerability Information
– Using Globally Verified Dedicated Vulnerability Testing Tool by Each Type of the System
C. Providing Professional Technical Assistance Service
– Professional Training for Practitioners to Build Self-vulnerability Test Capability
METHODOLOGY
Vulnerability Testing consists of 5 phases from Asset Identify to Treatment and Planning. Depending on the Target of Vulnerability Test, many testing techniques are used in the detailed steps of each phase.
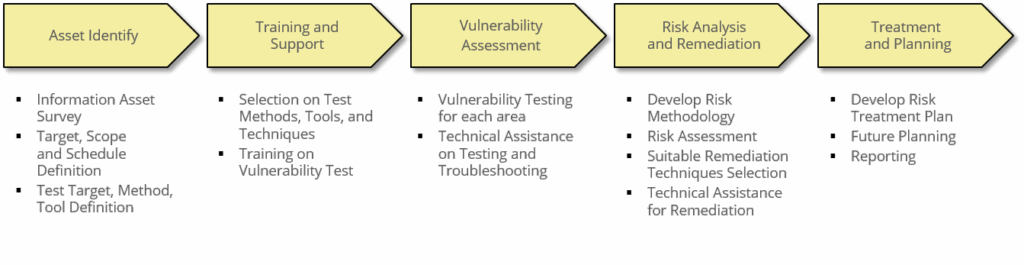
PROJECT CASE
Client :
SK Group Company
Vulnerability Test Type:
Web Application/Mobile APP Source Code Review
Testing target:
Internal and external Web applications and Mobile APP on operating(by automated tools and manual test)
Testing Techniques:
– Dedicated automatic testing tools to match the type of information system
– Manual testing of professional consultants
Testing Results:
Many vulnerabilities related to patches were found in security vulnerability testing using automation tools, but most security vulnerabilities related to business logic were found through manual testing rather than tools.
Peculiar Things
– Cross-checking with dynamic analysis of professional engineers based on static analysis results using automated testing tools
– In the dynamic analysis of expert engineers, more security vulnerabilities with higher severity has been found.
SECURITY SYSTEM DEVELOPMENT AND BUILDING SERVICE
EXECUTIVE SUMMARY
Most organizations that need to comply with security regulations must have a basic security system. In particular, the following articles from RURA describe the basic security systems you need.
Our Services and Products are sure to help you acquire security systems including technology transfer at low cost.
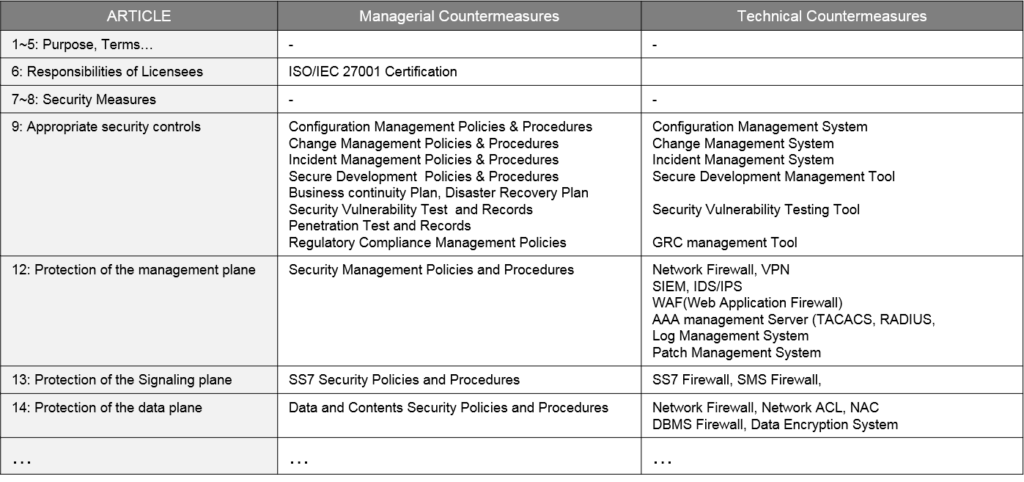
SERVICE STRATEGY
The security system development and building service provided by our company is definitely different from other companies. We are confident that this differentiation will help you acquire the necessary security system, not only cost point of view, but also from a future operational perspective.
A. Professional Consultant T / F Team Composition
– Because we develop and deliver security systems based on open source, you can acquire security systems at much lower cost than traditional commercial products.
B. Rapid development with globally proven Open Source
– Many years of experienced staff in ISO / IEC 27001 ISMS Assessment and Implementation
C. Provide not only simple system building but also related technology transfer
– Many years of experienced staff in ISO / IEC 27001 ISMS Assessment and Implementation
METHODOLOGY
The methodology consists of 4 phases from Requirements to Integrate Security System. Depending on the scope of project, there are a little bit deference tasks and steps of each phase.
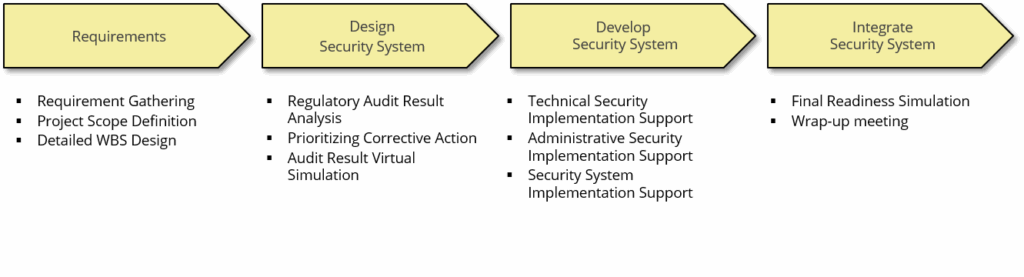
※ Deliverables
Security System Design Report, Security System Guide for administrators, Training and Education Materials
CASE – SECURITY SYSTEM DESIGN FOR A PUBLIC WEB SERVICE
One of the requirements of RURA Article 9 (Appropriate Security Com- ments) are the requirements for Secure applications. And the standard design of Security System for secure Web Service is designed as follows: Network security system to implement network access control, Database security system for database security, WAF for Web service security, and so on. We provide services to design and build security systems from a security threat perspective.

